LockBit 3.0: Revenge of the Bit
By: Austin Miller
It’s back again – LockBit 3.0 (also know as LockBit Black) is the newest variant of the LockBit ransomware that appeared just under a year ago. For people who need a refresher on the piece of malware or are new to the game, check out our full run down on how LockBit 2.0 works and how you should set up your security posture to counter it.
Of course, that information isn’t going to help you when it comes to this new ransomware. Thankfully, the people at Trend Micro were able to spot the LockBit gang reemerging and bringing with them improved capabilities – most worryingly, a range of capabilities which we would usually associate with BlackMatter. Despite this, however, security researcher Arda Büyükkaya – research team leader at Infinitum IT – was able to catch a sample of LockBit 3.0 and set off a group effort to analyze, understand, and neutralize this threat.
TL;DR?
Not got enough time to read our full breakdown? Here are a few bulletpoints to give you the broad strokes:
- The initial infection drops a .ico executable which loads the ransomware onto the system.
- After initial infection, all files are encrypted as normal.
- The ransom note has some oddities hidden in it, implying that this was made by a team outside of the Anglosphere or made as a manifesto from copy-pasting random pieces into the document.
- There is evidence that LockBit 3.0 has substantial pieces of code from BlackMatter, implying that malware gangs are attacking one another or they are working together to launch bigger attacks against organizations.
Understanding LockBit 3.0
First things first – it’s probably best to approach this malware with a clean slate in mind. It’s not so radically different from the older versions that it is unrecognizable, but it is certainly different enough to make this a redundant report. With that in mind, let’s get started.
Initial Infection
From initial infection, the LockBit 3.0 malware attempts to run a PowerShell command as such:
{04830965-76E6-6A9A-8EE1-6AF7499C1D08}[.]exe -k LocalServiceNetworkRestricted -pass db66023ab2abcb9957fb01ed50cdfa6a
If this is successful, the executable is dropped in the form of an .ico file into the %PROGRAMDATA% folder – this is where things start to get problematic.
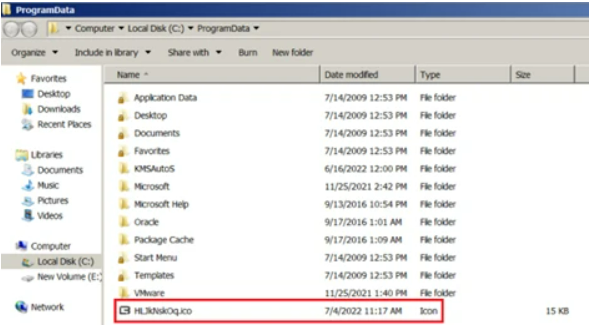
Encryption
The LockBite ransomware will get to work with encrypting files, appending a unique (malicious) file type, and changing file icons. The downloaded .ico file (named HLJkNskOq[.]ico) will start to append the file name as the file type for encrypted files, e.g., weddingphotos.jpg becomes weddingphotos.HLJkNskOq.
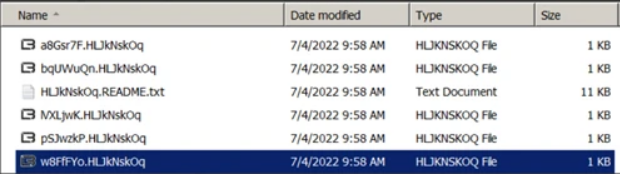
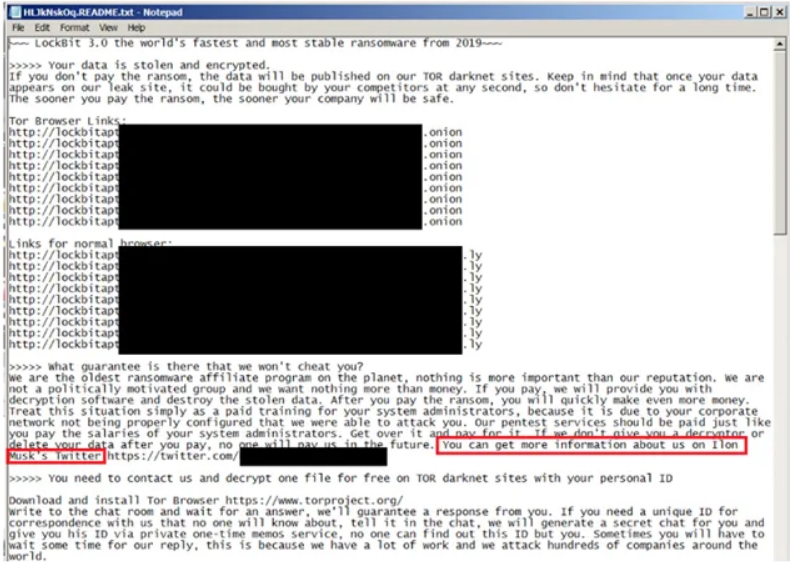
The Ransom Note
If there’s something I love more than a bizarre ransom note in a piece of malware, it’s a bizarre ransom note filled with gibberish and unusual sideways references to Western institutions. As you can probably guess, the LockBit 3.0 ransom note is truly one of the more confusing ransom notes that I have come across in recent years, in no small part because of its elusion to Ilon Musk [sic] and GDPR. References to data management are particularly bizarre in this case; the LockBit gang can accept extorting money from innocent victims, but they draw the line at improper data handling processes!
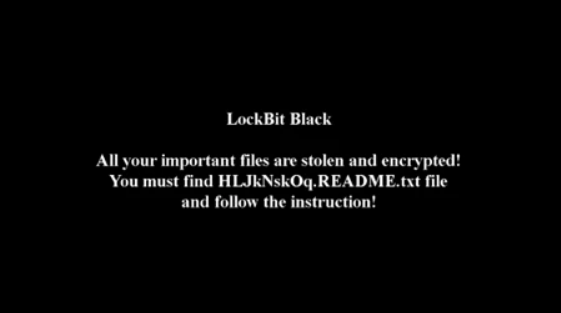
When this process has been completed, the following desktop wallpaper is loaded to the system.
As previously mentioned, this simple ransomware program is not quite as simple as it appears. Taking what seems to be considerable sections of code from another piece of ransomware – namely BlackMatter – shows us that either the malware gangs are starting to turn on one another or (more worryingly) they are creating more complex links that allow them to strengthen their arsenal. As identified by the Trend Micro team, LockBit 3.0 contains three distinct pieces of code that hearken back to BlackMatter:
- The strings used by LockBit 3.0 are a bitwise-XOR routine, a relatively simple process but one that was noticeable in BlackMatter.
- A separate bitwose-XOR and NOT routine.
- The decryption routine using a linear congruential generator (LCG) routine to create a key somewhat randomly.
These three separate functions can be seen here:
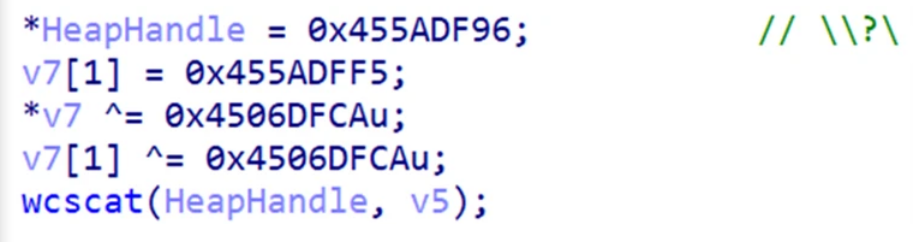
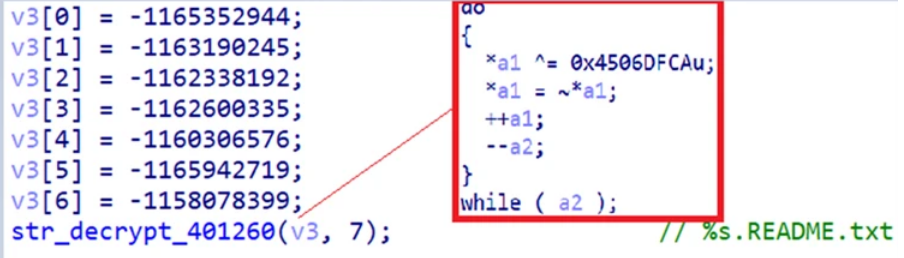
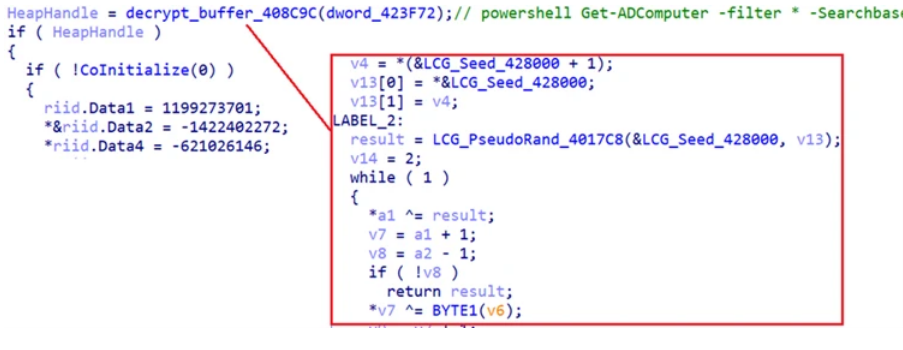
Now that we have a basic understanding of how LockBit 3.0 works and how it has taken substantial pieces of code from BlackMatter to strengthen its offensive capabilities, we will need to look into how exactly this piece of ransomware infiltrates systems and what the defensive side of the security game can do to protect itself against this threat. Next week, we will be breaking down LockBit 3.0’s procedures, processes, and techniques (PPTs) and exploring how you can harden your systems against this new threat.








