MITRE ATT&CK – System Information Discovery
Post Credit: Austin Miller
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.
Sun Tzu
This week, we’re looking at the 9th most common procedure in the MITRE ATT&CK framework – T1082: System Information Discovery. And just like the adversary knows their full offensive capabilities, they are keen to understand your defensive procedures too. Running the opposite of a threat intelligence campaign can give threat actors everything they need to run successful exploits – potential vulnerabilities, operating system information, host/user information, and a breakdown of the hardware you are using.
The truth is that once an adversary has breached defenses, system information discovery is extremely easy.
MITRE ATT&CK – System Information Discovery: what is system information discovery?
System information discovery is simply finding out the specifications about a target system. Having a piece of malware isn’t as easy as plug-in-and-play after a phishing attack – the malware must be launched on a system that is going to be affected by it. That’s why the adversary is constantly looking for relevant system information and how to integrate it into their malware procedures.
How can the adversary discover system information?
After entering the system, there are a number of ways the adversary can scan to find out more information. From a sample of 2,000 malware types, there are broadly three categories that all system information discovery campaigns fall into:
Systeminfo Discovery
For Windows systems, systeminfo is a utility that gives a full breakdown of all configuration information relating to the computer and the OS. This is a classic example of a living off the land attack – using the utilities and tools that the computer already has installed, therefore lowering the chances that malicious behavior will be noticed. The list of information that can be gleaned from this type of discovery includes:
Operating system configuration
OS name
-
- OS version
- OS manufacturer
- OS configuration
- OS build type
- Registered owner
- Registered organization
- Original install date
- System locale
- Input locale
- Product ID
- Time zone
- Logon server
Security information
-
- Hotfixes
Hardware properties
-
- RAM
- Disk space
- Network cards
- Processors
- Total physical memory
- Available physical memory
- Virtual memory
Other system information
-
- System boot time
- System manufacturer
- System model
- System type
- BIOS version
From something as little as running systeminfo on the command prompt, the adversary could easily find outdated OS installs or scrape information to be sent to a Command and Control (C2) server. The latter option is exactly what the Zxshell Remote Access Trojan (RAT) did – running espionage operations over a large network of victim hosts, the RAT identified and integrated targets into the Group 72 network by sending hostname, organization, OS details, CPU speed, and total physical memory figures back to the C2 server.
Systemsetup Discovery
For macOS users, a series of different commands can be used to gain access to mission critical information for the adversary. These include:
-
- -getcomputername
- -getremotelogin
- -getlocalsubnetname
- -gettimezone
Other commands can be used, but macOS is more difficult to infiltrate than Windows. All these commands require administrator access to run, meaning that there is at least some level of defense built into Macs.
Iaas API Call Discovery
With the expansion of cloud Infrastructure as a Service (IaaS) platforms such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), the adversary has found new ways to identify and exploit vulnerabilities. Using APIs to access the big-name cloud vendors has been surprisingly easy, as exemplified in the following examples.
AWS
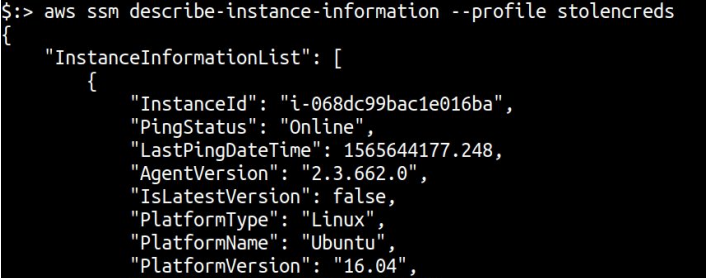
Using the Describe-instance-information API action with an AWS IaaS allows the adversary to pull down the following information:
Azure
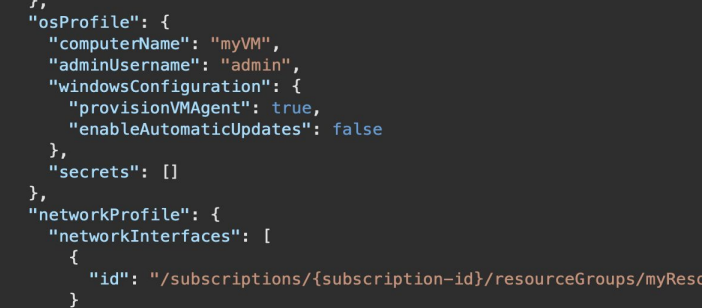
On the other hand, accessing vital information on Microsoft Azure products can be achieved through Virtual Machines – Get operations. When this type of LotL attack happens, the following information is accessible:
How has the adversary used information gained during system discovery?
Along with the ZxShell attack that was referenced above, the following malware types are known for using System Information Discovery to turn the screw on data infiltration and destruction.
Sodinokibi
The now infamous Russian ransomware creates a unique identifer (UID) for every infected victim based on the volume serial number and the CPUID, as well as collecting username, hostname, domain name, locale, keyboard layout, OS name, hard disk details, and CPU architecture. When dropping the ransom note, the UID is used to process parts of the payment URL. The UID also triggers to bro parameter, which turns true if the system has a CIS-aligned language pact installed (presumably taken from keyboard layout information).
Mekotio
The banking Trojan Mekotio also weaponized system information by collecting the following:
-
- Firewall configuration
- User privileges
- OS name and version
- Installed anti-fraud protection products
- Install anti-virus/anti-malware programs
- Local time
This information is then used to whitelist systems that are protected against the Trojan.
Although these are only two examples of the adversary collecting and using system information against their victims, the ability to collect information about a target empowers threat actors. Learning to protect your systems and stop them from handing out information that turns your otherwise hardened network into an easy payday for cybercriminals.
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes. Join the newsletter here.








