A Guide on Using Nuclei – a YAML based Vulnerability scanner
Written By: Indrajeet Bhuyan
Automation is a favorite topic for most cyber security enthusiasts. We like to automate most of the boring stuff. Some people automate so that they don’t have to waste time doing the repetitive task while others automate as they are just too lazy to do the task . But whatever be the reason, automation is getting popular in the Cyber security field. So popular that you can find in many job descriptions today where they ask you if you have got automation skills.
Today I would like to introduce an interesting tool that can automate a lot of things for you. A lot of bug bounty hunters already use this tool to find quick low hanging fruits ( bugs ). Let me introduce to you Nuclei.
Nuclei is a community-powered, fast and customizable vulnerability scanner. Just like most modern security tools, Nuclei too is built in Go lang for faster processing. Nuclei works on YAML-based templates which leads to zero false-positive results and provides fast scanning on various hosts.
In this article, we will learn how to install Nuclei, use the tool to find a quick bug, and also explore its templates.
Install Nuclei
Step 1: As Nuclei is a Golang-based tool so you need to first install Golang in your system. Once it is installed you can run the following command to see Golang is installed correctly
go version
Nuclei require go1.17 to install successfully.
Step 2: Now run this command to install Nuclei
go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Once this is done Nuclei should be installed. You can verify if nuclei is installed successfully by typing the command nuclei -h. If you face any issues while installing you can always check their GitHub repo here: https://github.com/projectdiscovery/nuclei
Once Nuclei is installed you can check the nuclei’ inbuilt templates by going to nuclei-templates
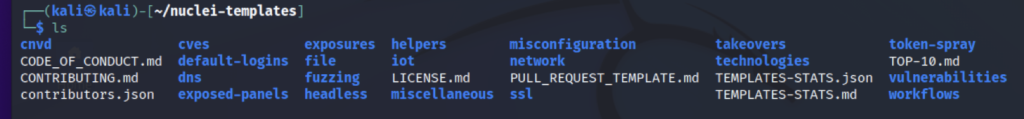

You can see that it contains a good number of pre-built templates contributed by 300+ security researchers and engineers which you can use. All the templates are divided into different categories like Fuzzing, Vulnerabilities, CVEs, etc.
Here is how a Nuclei template looks like
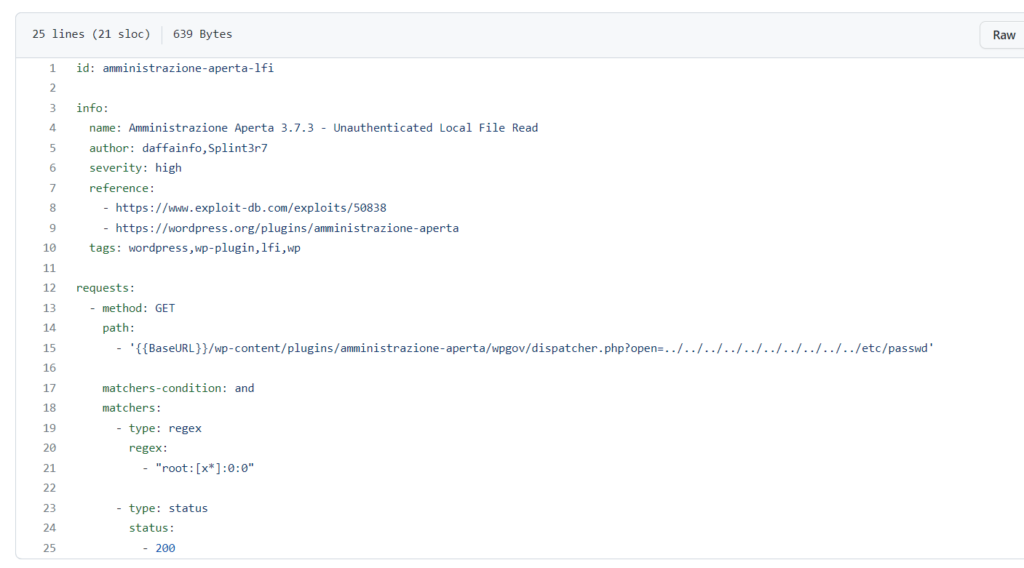
One can easily create their own template based on the requirement.
Each template present in Nuclei has a unique ID which is used during output writing to specify the template name.
The best part about Nuclei is that it offers to scan for a variety of protocols like TCP, DNS, HTTP, SSL, File, WHois, Websocket, Headless, etc.
Running Nuclei
By default, nuclei run all the templates against a target but we get the option to specify which template to use.
- Scan a single website with a single template
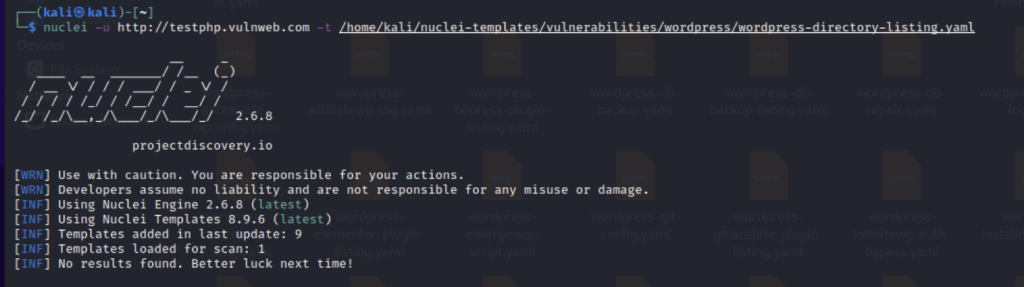
nuclei -u http://example.com -t vulnerabilities/wordpress/wordpress-directory-listing.yaml
This will run the template WordPress directory listing for the website and show results
- Scan a single website using multiple templates
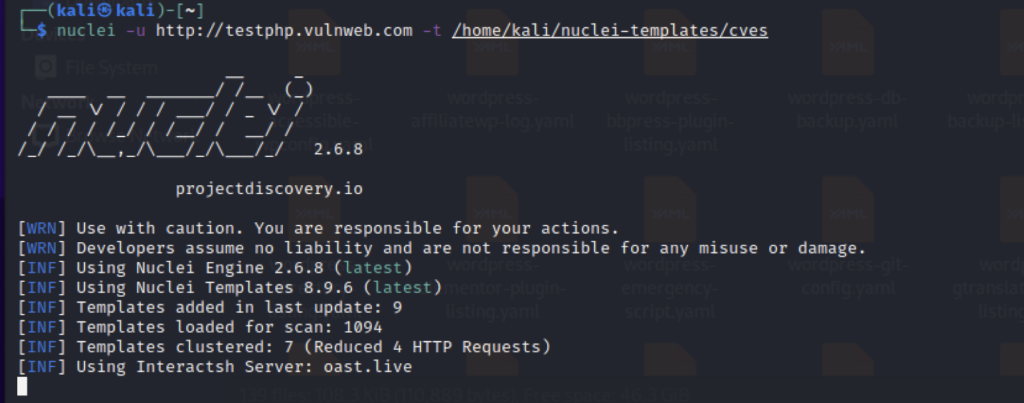
nuclei -u http://example.com -t cves/
Here nuclei will scan the website against a list of CVEs to see if it is vulnerable to any of the CVEs present in their list
- Scan multiple websites with a single template
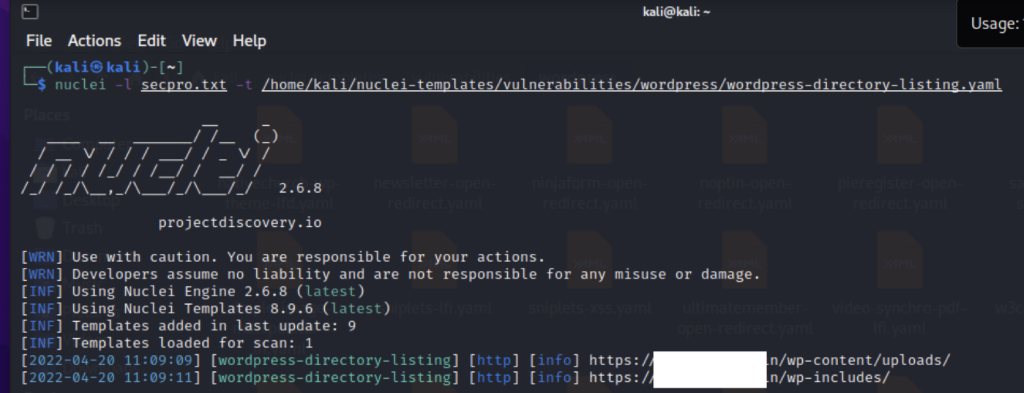
nuclei -l domains.txt-t vulnerabilities/wordpress/wordpress-directory-listing.yaml
Here nuclei will take the list of domains from domains.txt and test the wordpress directory listing against it.
- Scan multiple websites using multiple templates
The main power of nuclei comes here. We can feed in a large number of domains and let nuclei scan them with all the templates available
nuclei -l domains.txt-t vulnerabilities
This command will use all the templates available in the vulnerabilities folder against all the domains present in the domains.txt list
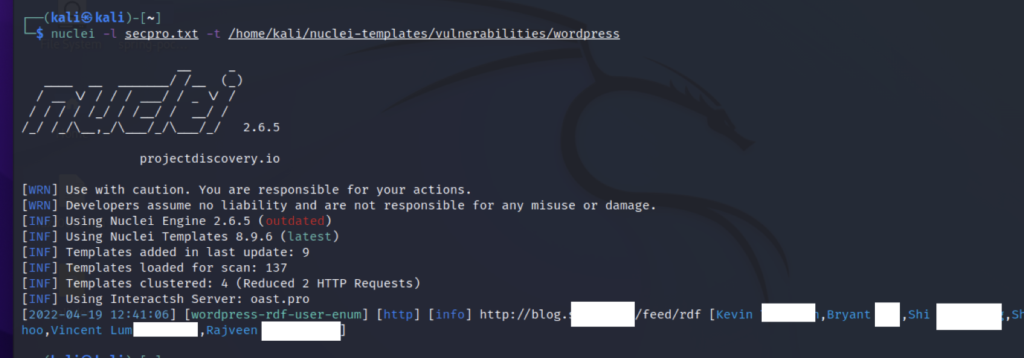
Demo
Here for the demo, I used nuclei to find some wordpress based vulnerabilities. I made a list of a few websites running WordPress and ran Nuclei on it.
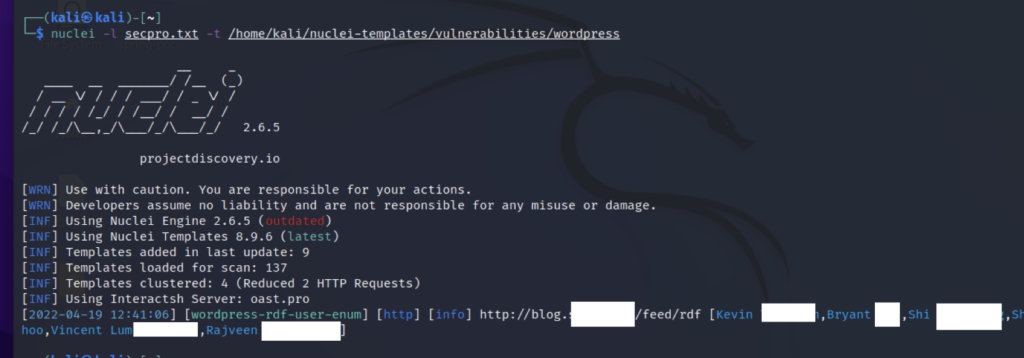
Here we can see that Nuclei found a user enumeration flaw in the WordPress based website and displayed us the name of the users.
Here is an example of how Nuclei is used by a bug bounty hunter to automate his bug hunting.
Mohamed Elbadry created a cache poisoning template in Nuclei
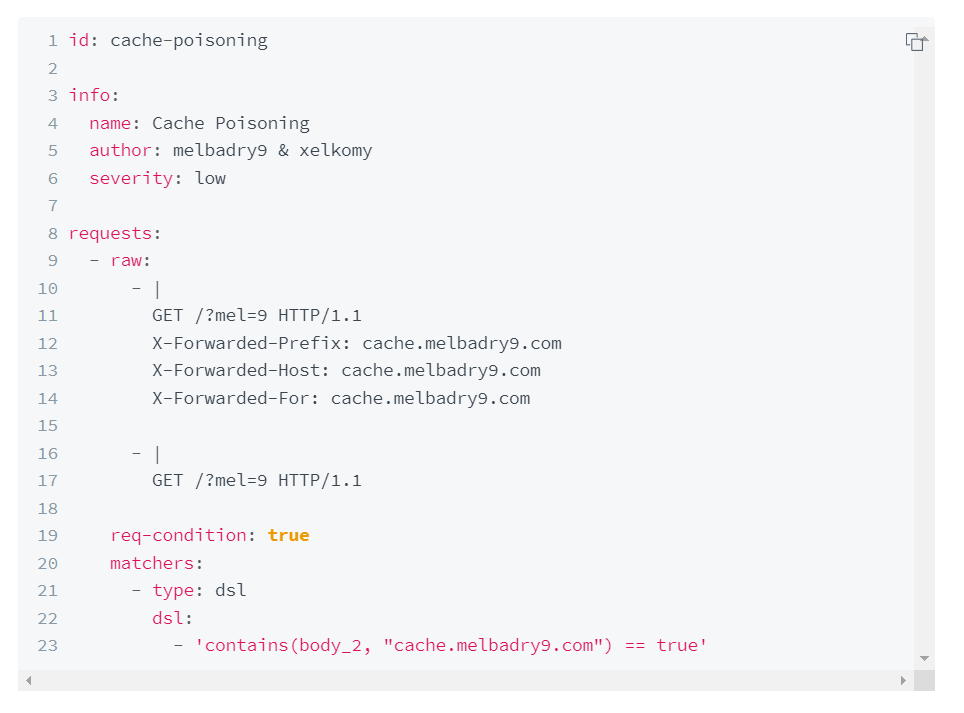
As Nuclei templates are YAML-based so it’s easy to understand. We can easily understand the logic of this template. After creating this template he made a list of 4957145 alive subdomain that runs public/private bug bounty. After he made the list of domains he ran nuclei to test this template against these 4957145 subdomains.
After keeping it running for half a day he found that one of the subdomains was vulnerable. He quickly reported the flaw and received a bounty of USD 1500
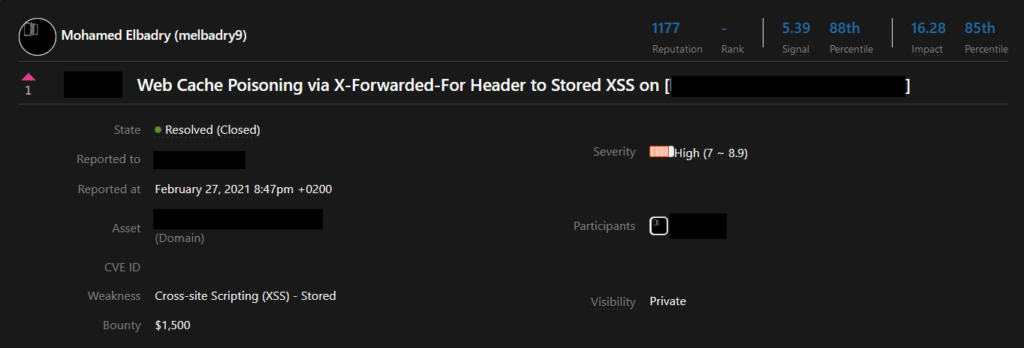
Read his full writeup here: https://blog.melbadry9.xyz/write-ups/fuzzing/nuclei-cache-poisoning
Conclusion
Nuclei is a powerful YAML-based vulnerability scanner. The active community who regularly contributes different templates and the power to create their own template makes this tool very powerful. If you have not yet used this tool I recommend you give it a try. In the article, I have only given a brief introduction but a lot more can be done. Visit their official page to learn more about this tool.








