Another entry into our OSINT Top Ten is an extremely simple tool which will allow you to gather information about suspicious IP addresses and investigate whether certain individuals should be trusted or not. This tool should be immediately useful to anyone working in any public-facing industry, but we’re going to run through some ways to use it too.
ThreatJammer is a Data Enrichment API, according to their developers. Useful as a tool for collecting high-quality data concerning threat intelligence, it is one of the best ways to detect and stop malicious activity from affecting applications, servers, and other systems. It is completely crowdsourced, meaning that all information flowing through the web application comes from like-minded security-conscious people like yourself.
Why should I use ThreatJammer?
As you can expect from an OSINT tool, ThreatJammer relies on OSINT lists to build an effective threat intelligence gathering kit. This involves using crowdsourcing techniques to build a community blacklist which can be connected to access control tools, content delivery networks, honeypots, and proxy servers – basically anything you can attach an API to. Handy!
In addition to this, the team behind the web application also put together closed-source intelligence (CSINT) datasets too. This is based on information available on the deep web or hacker forums, where the adversary lies in wait. Because these places can sometimes be a minefield to navigate, this service is essential for people trying to gather sensitive data without running risks on their own or on organizational systems.
How does ThreatJammer work?
Using the ThreatJammer interface is very simple – when you connect to the website, you will see a zero to one hundred threat scale and a box to enter in an IP address. This is the basic set up for the ThreatJammer tool and presents it quite clearly as a simple tool that can be quickly referenced.

If you have an IP address that you want to test out, you can simply type it into the box. But if you’re on a more generic threat intelligence gathering mission, this webpage also has a number of the crowdsourced and freely available suspicious IP addresses logged in another window. In this way, you can check out what everyone else is saying and steal some of the freely available content for your own security posture.
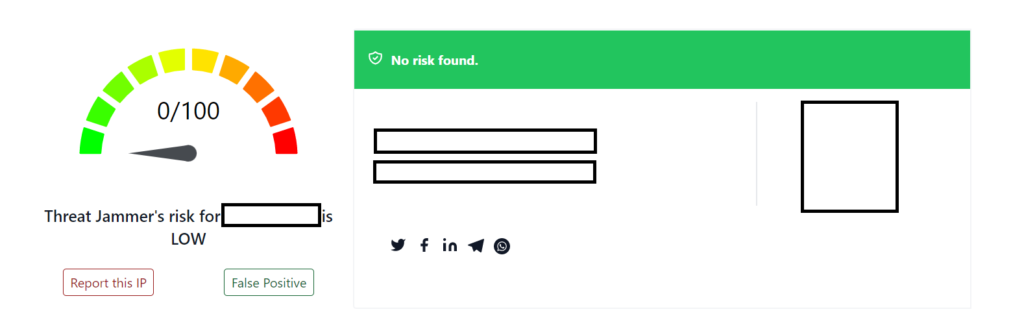
Of course, the best place to start is with your own IP address. I’m happy to report to all secpro readers that I have a squeaky clean IP address that does not set off any alarms in the ThreatJammer camp. I’ve obscured the relevant personal information that ThreatJammer displays in the above image, but you should get a feel for what a “false alarm” screen should look like in your threat intel ventures with ThreatJammer.
Of course, I expected that of my home address. But how does the system work when there is a high-level threat? What should I expect to see if a suspicious IP address is knocking on the door of my network? I took an IP address from the crowdsourced denylist and typed it into the search bar on the first web page.
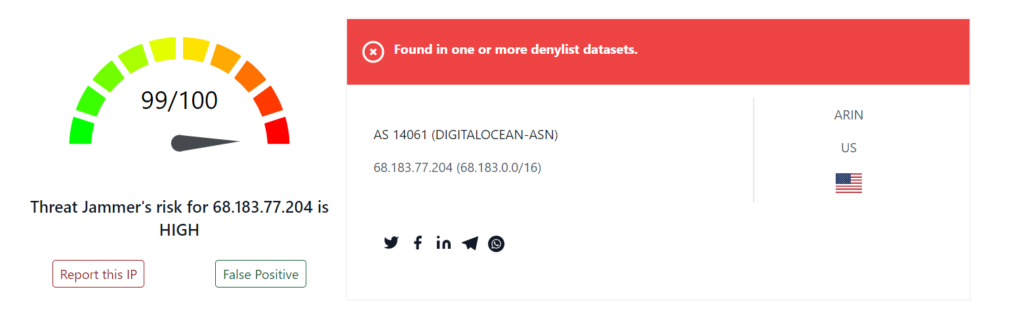
When the page has loaded, you will see the same style of page, but now the relevant information is contained within a red box and the threat scale is now sitting on the far right – it seems safe to say that the ThreatJammer community shared a particularly nasty IP address here! From the information box, you can gather information about the provider, the source area, and even report it as a false positive if you believe that is the case. A very useful tool that helps others just like you all around the world.
Should I use ThreatJammer?
As with all narrowly aimed OSINT tools, there are obvious restrictions to what ThreatJammer can achieve. It’s not going to massively improve an existing IT team which has its processes in place and can perform all these functions through a variety of in-house tools or expensive third-party solutions. But, for people that are attempting to build a security suite without spending much money, tools like ThreatJammer are a fantastic way to keep costs down without sacrificing quality.
Knowing how to use ThreatJammer is an excellent way to keep an eye on the kind of IP addresses that are attempting to connect to your server. It requires some manual work, but it can be integrated into a number of other tools which allow you to keep a close eye on your essential systems. To find out more about ThreatJammer, consult their blog at threatjammer.com/tutorials.








