Polkit Vulnerability CVE-2021-4034
In our latest look at vulnerabilities we review another CVE aimed at the Linux Operating System. Polkit affects all major Linux Distributions running any version of Polkit. In a Linux environment Polkit, previously known as PolicyKit is a system service the controls system-level privileges by using policies to determine if a user has the given privileges to undertake certain actions. Relying on the pkexec executable, a SUID-root program installed by default on all major Linux Distributions. By exploiting Polkit adversaries can elevate privileges on a target system. Red Hat list the following versions as affected in this security bulletin: https://access.redhat.com/security/vulnerabilities/RHSB-2022-001.
- Red Hat Enterprise Linux 6
- Red Hat Enterprise Linux 7
- Red Hat Enterprise Linux 8
- Red Hat Virtualization 4
Additionally, any Red Hat product supported on Red Hat Enterprise Linux including RHEL CoreOs is also potentially impacted. Describing the vulnerability Red Hat explain that the pkexec program does not validate the number of arguments passed which eventually leads to environment variables being executed as commands. When exploited this leads to arbitrary code being executed as a privileged user, granting the attacker a local privilege escalation. When starting a new process, the Linux Kernel will create an array with the command arguments (argv), and another with the environment variables (envp, with an integer value representing the argument count (argc). The Linux Kernel positions both the argument array and the environment variables array in a contiguous way in memory. A further default behaviour is how the first value of the argument array contains the executable name (pkexec for pkexec executable), with this implying any arguments sent to the process by the user are positioned after this value.
CVE-2021-4034
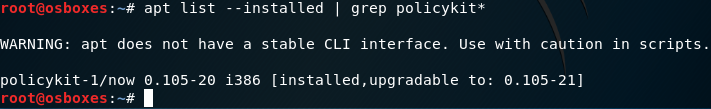
Discovered by the Qualys Research Team and publicly disclosed on 25th January 2022, due to the vulnerability allowing privilege elevation of a user on a system it was given a high CVSS score of 7.8. To understand if a system is vulnerable the following commands should be run to check which version of Polkit is installed. Any version below 0.120.r2 is vulnerable depending upon the Linux Distribution:
#apt list –installed | grep policykit*
#yum list installed | grep policykit*
#dnf list installed | grep policykit*
example:
Mitigation
Two methods to mitigate the vulnerability risk exist, either by applying the patching via official sources or manually using instructions detailed below:
Red Hat Product Security strongly recommends affected customers update the polkit package once it is available. For customers who cannot update immediately, the issue can be mitigated by executing the following steps:
1. Install the following required systemtap packages and dependencies: https://access.redhat.com/solutions/5441.
2. Install polkit debug info:
debuginfo-install polkit
3. Create the following systemtap script, and name it pkexec-block.stp:
probe process(“/usr/bin/pkexec”).function(“main”) {
if (cmdline_arg(1) == “”)
raise(9);
}
4. Load the systemtap module into the running kernel:
stap -g -F -m stap_pkexec_block pkexec-block.stp
5. Ensure the module is loaded:
lsmod | grep -i stap_pkexec_block
stap_pkexec_block 434176 0
6. Once the polkit package is updated to the version containing the fix, remove the systemtap generated kernel module by running:
rmmod stap_pkexec_block
After using the rmmod command, a system reboot isn’t required.
Note: If the system is rebooted, the module generated by the systemtap needs to be reloaded into the kernel. To do that, navigate to the directory where the mitigation script was created and follow steps 4 and 5.
Once the mitigation above is performed, pkexec will continue to work as expected for legitimate use cases.
- Official Patches
Use the following links for your Linux Distribution
Ubuntu https://ubuntu.com/security/notices/USN-5252-1
Red Hat https://access.redhat.com/security/vulnerabilities/RHSB-2022-001
Debian https://security-tracker.debian.org/tracker/CVE-2021-4034
SUSE https://www.suse.com/security/cve/CVE-2021-4034.html
Update via Command Line
- APT
- sudo apt install policykit-1
- sudo apt update && sudo apt upgrade
- YUM:
- sudo yum install policykit-1
- sudo yum update && sudo yum upgrade
- DNF:
- sudo dnf install policykit-1
- sudo dnf update && sudo dnf upgrade
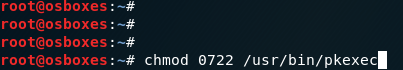
If it isn’t possible to apply patches or mitigate using the manual method you can also strip the pkexec of the setuid bit as a temporary measure. To do so use the following CLI commands
chmod 0755 /usr/bin/pkexec
Proof of Concept
Just as you would expect several Proof of Concept Repos are available publicly via GitHub if you wish learn more, or to exploit this vulnerability in a lab environment you can clone the repo below or look to find another example.
https://github.com/arthepsy/CVE-2021-4034








