The starting point and one of the most common things of any bug bounty engagement is reconnaissance. Reconnaissance helps us know more about the target and help us determine what steps to take to move ahead with the target.
Security professionals often spend a good number of time doing recon on the attack surface. For this purpose people generally use multiple tools and often different tools are used to get different information. For example, one can use a subdomain finder tool to get all the subdomains and use a screenshot tool to get a screenshot of all the subdomains.
As all the information is scattered in different places often it becomes difficult to go through every piece of information and make sense of it.
Today I’ll introduce you to a tool called reNgine. reNgine is an automated recon framework designed for obtaining information during web application penetration testing. It provides customizable scan engines to scan domains, and endpoints, or collect data. The framework’s advantage lies in its ability to consolidate all gathered information in one location through a highly adaptable reconnaissance pipeline.
Utilizing reNgine can be advantageous when conducting reconnaissance activities such as endpoint gathering, directory and file searches, screenshot capture, and consolidating the resulting information in a single location.
Steps to install reNgine
reNgine uses several scripts and tools, those tools or scripts rely on various tools to be installed like Go, Python, etc, and to avoid any dependency issues, docker can be used. Using Docker will not only ease the dependency issues but will also ease the installation steps.
reNgine requires docker, docker-compose, and make to be installed before you begin installing reNgine.
Once the prerequisites are done we can start installing reNgine
- Clone reNgine
git clone https://github.com/yogeshojha/rengine && cd reNgine
- dotenv file
Edit the dotenv file using nano .env or vi .env or vim .env.
The sample .env file can be found here.
- Generating SSL Certificates
reNgine runs on https unless otherwise used for development purpose. Using https is recommended. To generate the certificates you can use
sudo make certs
- Build reNgine
To build the reNgine, use the following command
sudo make build
- Run reNgine
Once the build process is successful, we’re good to run reNgine. This can be done using the below command
sudo make up
- Registering an account
You will need to create a username and password to log in to the reNgine. To register reNgine, run the following command
sudo make username
Now you can visit 127.0.0.1 to access reNgine.
Features of reNgine
Here are some of the features of the reNgine tool:
Automated Reconnaissance: reNgine automates the reconnaissance process and saves time during web application penetration testing.
Customizable Scan Engines: It provides customizable scan engines to scan domains, and endpoints, or collect data as per user requirements.
Consolidation of Information: reNgine consolidates all the gathered information in one place, making it easy for the user to analyze and act on the data.
Highly Adaptable Pipeline: The framework’s pipeline of reconnaissance is highly customizable, allowing users to tailor the reconnaissance process to their specific needs.
Directory and File Search: It provides a directory and file search feature, allowing users to locate and download sensitive files from the target web application.
Screenshot Capture: reNgine can capture screenshots of the target web application’s pages, allowing users to visualize the application’s layout and identify potential vulnerabilities.
Integration with Other Tools: It can integrate with other tools like Nmap, Dirsearch, and others to enhance the reconnaissance process.
Reporting: reNgine generates reports that provide a summary of the reconnaissance process, including vulnerabilities, endpoints, screenshots, and other important information.
Cross-Platform: reNgine is a cross-platform tool that can be used on Windows, Linux, and macOS systems.
Using reNgine
Once you open 127.0.0.1 you will get the login page where you can log in using the username and password that you set in the above steps:
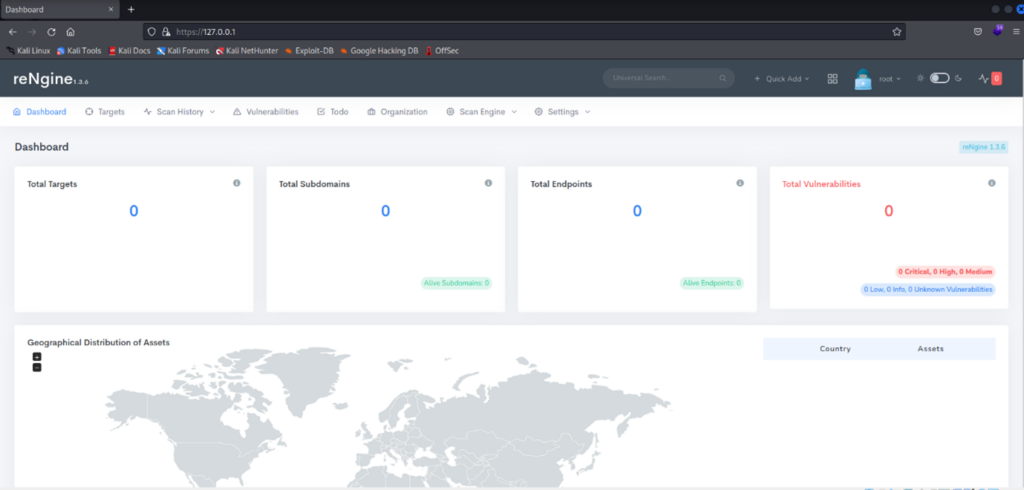
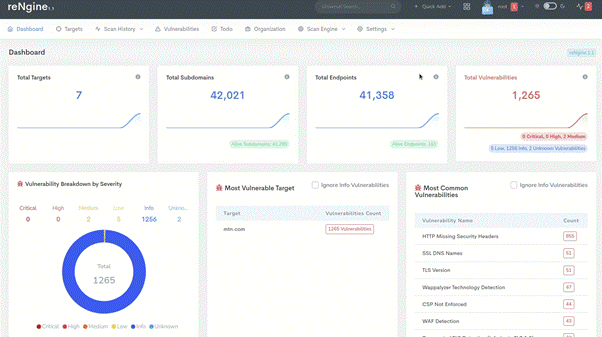
Once you are logged in you can see the dashboard. The dashboard is very user-friendly and shows everything that is happening. Since you logged in for the first time there won’t be much.
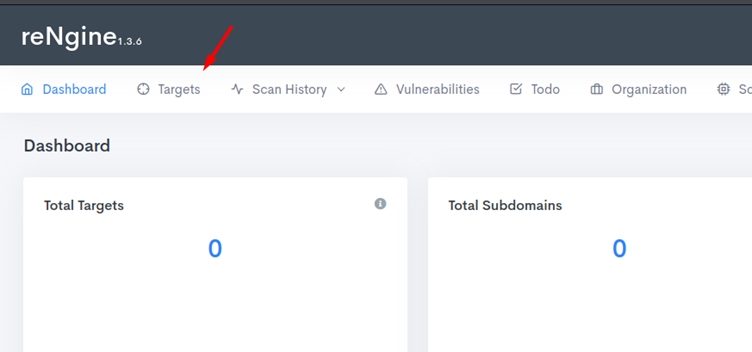
Now you can click on targets and set a target first. Once the target is set then we can perform different activities on it.
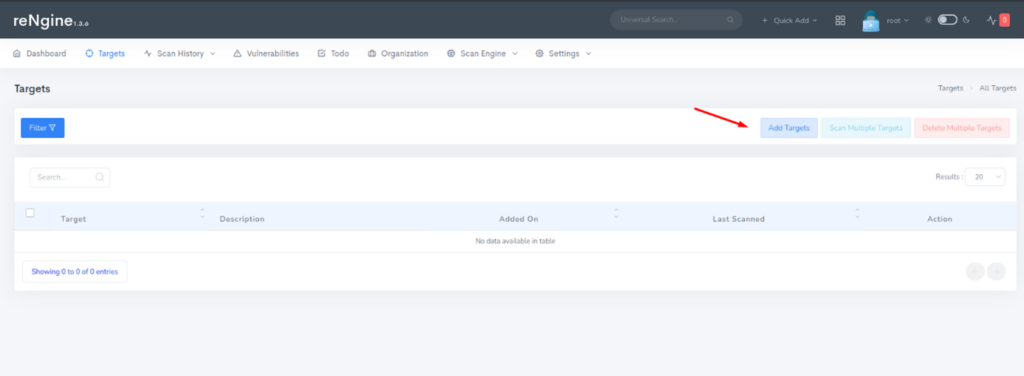
Here, for example, we have used Packt’s website URL:
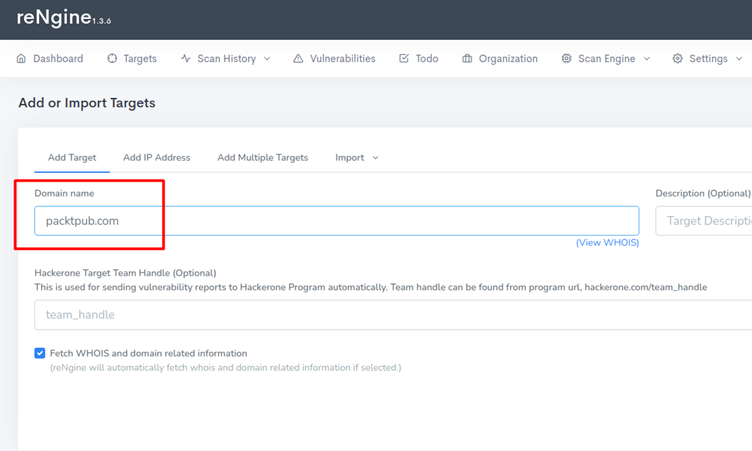
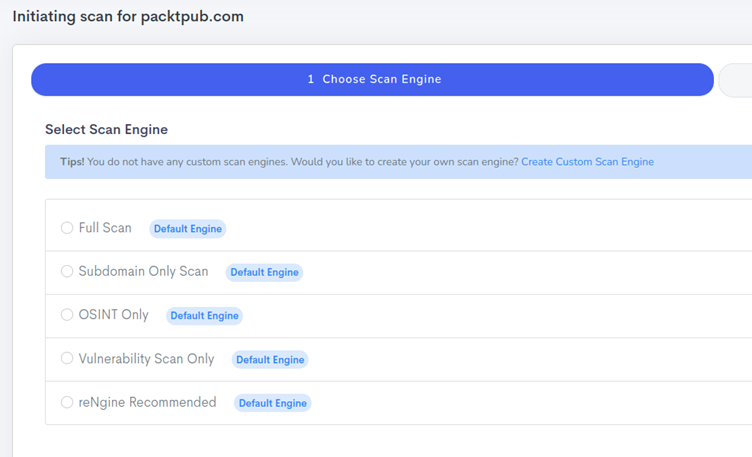
Once the target is added it will ask you for some more information. We can select some pre-defined engines to use for our scan. Some engines that reNgine provides are :
- Full Scan
- Subdomain only scan
- OSINT only scan
- Vulnerability Scan
- reNgine recommended Scan
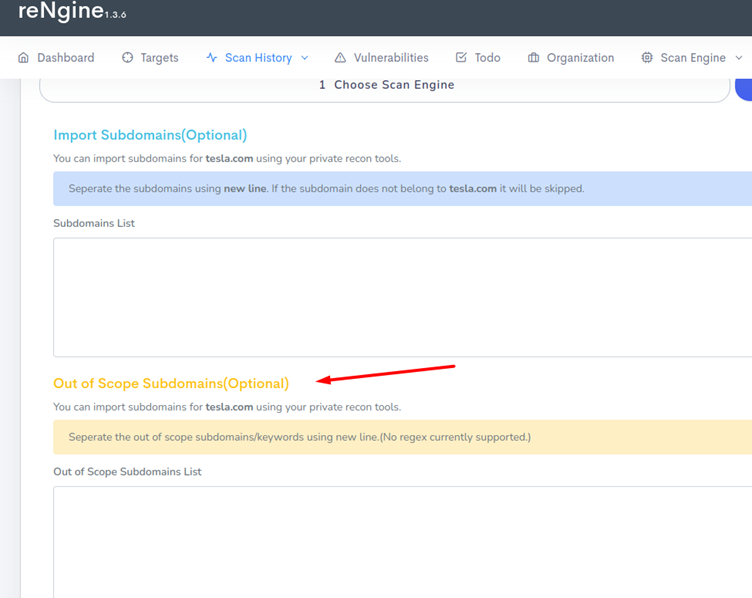
Once the engine is selected it will ask us to enter some more information like exclude URL. Now, this feature is important because in most bug bounty programs the company doesn’t want bug hunters to try all URLs. So here we can define which URLs not to touch.
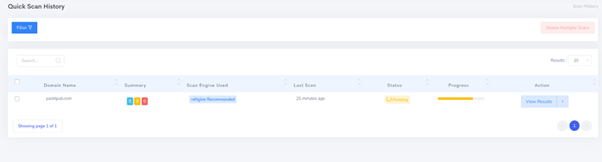
Once the scan starts it will show a progress bar and we need to wait till the scan is complete. The scan completion time depends on the target size, engine selected, etc.
In conclusion, reNgine is an automated recon framework that provides customizable scan engines to scan domains, and endpoints, or collect data, making it easier for security professionals to conduct reconnaissance activities during web application penetration testing. The framework is highly adaptable and consolidates all gathered information in one location, making it easier for the user to analyze and act on the data. With features like directory and file search, screenshot capture, integration with other tools, reporting, and cross-platform compatibility, reNgine is a valuable tool for bug hunters and security professionals. Its user-friendly interface and step-by-step installation guide make it easy for users to get started with the framework.








