SecPro #16: Detection and Response for ProxyShell and LockFile, Antivirus Bypass Techniques
In this Issue
→ 5 Tools You Should Use for Container Security and Compliance
→ Detection and Response for ProxyShell and LockFile
→ Antivirus Bypass Techniques with Python
→ Recent Security Issues
→ Secret Knowledge
→ The Puzzle Section
Thoughts from the Community
Thank you for the overwhelming responses and feedback on the SecPro. Here’s what some of our smart, curious SecPro ambassadors have to say about the past issues:
SecPro #13
“I really liked the discussion of good hash. It is important today for data integrity. Many people use wrong hash. Personally like to see more use of digital signature. Also liked the Nessus scan article.” – Joseph
“The Nessus tutorial was great, same for the Python content. Secret knowledge is a cool new section. Overall I enjoyed this newsletter more than the previous one.” – Mark
SecPro #14
“I found the descriptive text of Conti malware fascinating.” – Randy
“Enjoyed Mimikatz. Secret knowledge. Discovered new tools“. – Livio
SecPro #15
“Maintain the current level. Possibly more technical content.” – Talarczyk
“Email security is always useful. Got 3 new clients this week just because they got ransomware by spoofed phishing emails and decided to bring in external help.” – Anonymous
Container Security
5 Tools You Should Use for Container Security and Compliance
Securing containers is a nightmare – 94% of companies who are using containers have reported at least one security incident in their Kubernetes environment in the past 12 months. Containers are volatile but incredibly useful for DevOps teams, so how can we secure them?
1. Cosign
Signatures are necessary in the world of container management, so the team behind Cosign is trying to make them part of the invisible infrastructure. What does that mean exactly? All container images (regardless of the platform) will be signed, verified, and stored in a vetted OCI registry, allowing developers to safely source and download secure containers.
As part of the larger sigstore organization, Cosign is easy to install, easy to use to sign a container, and easy to search for known signatures against container images. This makes the security analyst’s job easier and speeds up the process from finding the right container to production.
Need to check over the details before implementation? Take a look at the Detailed Usage documentation available on Github.
2. Harbor
An open-source registry for building, scanning, and securing artifacts with policies and RBAC, Harbor is a key tool for securing container platforms like Kubernetes and Docker.
Harbor’s main use cases are:
- Security and vulnerability analysis in images for container platforms
- Content signing and validation for approved images
Implementing Harbor into your workflow allows a security team to consistently distribute secure images across an organization without fears of vulnerabilities, wonky RBAC settings, or opportunities for privilege escalation.

Harbor scanning pipeline
Harbor was built using multiple open-source tools that create an easy-to-implement workflow for a DevSecOps team.
What to find out more about Harbor? Check out this webinar by the team behind the tool.
3. Inspektor Gadget
Originally designed to service the Lokomotive Kubernetes distro, Inspektor Gadget is a collection of debugging and inspection tools that works with all forms of Kubernetes.
Capable of snooping IPv4 and IPv6 syscalls, generating network policies, profiling CPU usage, and suggesting security capabilities (along with other functions through a variety of gadgets), Inspektor Gadget is an open-source toolkit that secures and monitors your K8s containers and pods.
Here’s a link to an example of the Inspektor Gadget opensnoop tool in action.
Pushed as a “strace in the past” tool, tracing is permanently enabled. This allows for easier management and monitoring so you can make sure that your deployed distros are fitting with your security needs.
4. PodSecurityPolicy
Not all necessary tools need to be third-party – the in-built Pod Security Policy tools (made available through kubectl) are perfect for implementing group policy styles settings on all containers and pods.
Managed from either PodSecurityPolicy or securityContext, you can implement:
- Privileged flag prevention, including overwriting privileges allowed in the containers natively
- Host PID/IPC namespace, networking, and ports blocking, allowing you to stop your containers from leaking information to threat actors
- Limited filesystem use on the host machine
- Privilege escalation prevention
- Rejection of containers with root privileges
And a whole host of other useful security settings that help you manage the most common security problems containers bring.
Want to find out more about implementing Pod Security Policy Tools in your organization? Check out Kubernetes’ documentation here.
5. Distroless Docker Images
Another tool that isn’t so much a security tool as a preventative measure, Distroless Docker images are images that only contain the application and its runtime dependencies. Because so many issues that come about with Docker are based on the underlying OS requesting privileges, these images are excellent for stopping vulnerabilities dead in their trackers.
Mimicking best practices that are employed by Google and other tech giants, Distroless Docker images are:
- Small
- Package manager free
- Shell free
- Free from all other programs you might expect with common Linux distros
This means that managing containers with other useful tools like Inspektor Gadget is even easier – there are no extra parts that will attempt to make inappropriate requests or given threat actors a jumping-off point!

Excerpt from Distroless Docker images Github page
These tiny Docker images were also built by someone with a sense of humor – check out the full page here.
Not only are these images tiny which allows for less strain on IT resources, but they are also signed and verified by Cosign (another SecPro favorite).
Special thanks to Austin Miller.
Indicators of Compromise
Detection and Response for ProxyShell and LockFile
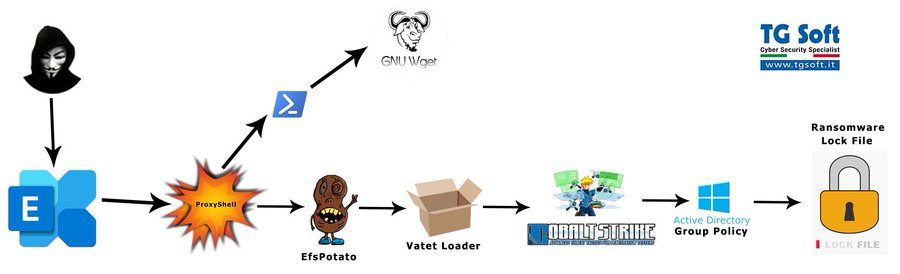
Earlier this week, the Cybersecurity and Infrastructure Security Agency (CISA) released an urgent notice related to the exploitation of ProxyShell vulnerabilities (CVE-2021-31207, CVE-2021-34473, CVE-2021-34523). By chaining these vulnerabilities together, threat actors are compromising unpatched Microsoft Exchange servers and gaining footholds into enterprise networks.
Adversaries exploit the above-mentioned vulnerabilities and attempt to install webshells – web content, served on-demand, that functions similarly to backdoors. Using these web shells, adversaries inherit the privilege level of the Exchange IIS web server to perform reconnaissance, harvest credentials and pursue post-exploitation behavior such as installing ransomware.
Vendors and researchers are also observing these attacks tied to post-exploitation behavior such as deploying ransomware to victim environments. Here are some of those findings and key takeaways to help you in your Detection and Response efforts:
Kevin Beaumont
Researcher Kevin Beaumont first spotted that ProxyShell was being exploited from 209.14.0[.]234 on August 13. In this post, Kevin shares that these vulnerabilities are worse than ProxyLogon, the Exchange vulnerabilities revealed in March — they are more exploitable, and organizations largely haven’t patched. This post also shows how you can identify systems and defend your organization.
The ProxyShell and LockFile link was also mentioned in this Twitter thread.
Symantec
The Broadcom/Symantec threat hunter team indicates that the attackers gain access to victims’ networks via Microsoft Exchange Servers, and then use the incompletely patched PetitPotam vulnerability to gain access to the domain controller, and then spread across the network. It is not clear how the attackers gain initial access to the Microsoft Exchange Servers.
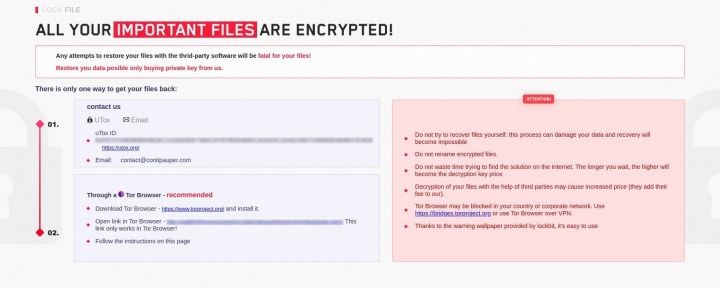
The attackers behind this ransomware use a ransom note with a similar design to that used by the LockBit ransomware gang (Figure 1) and reference the Conti gang in the email address they use – contact@contipauper[.]com.
Elastic Security
The Elastic Security team identified indicators of compromise (IoCs) indicating similar activity as reported by the industry. The details of this activity can be found in their Discuss forum.
Elastic observed unusual descendant processes (cmd.exe and poweshell.exe) of the Exchange IIS webserver process (w3wp.exe) that involved notable remote network indicators to high-numbered ports:

Detection and Response for ProxyShell and LockFile: Process ancestry of Exchange server exploitation
If you use Elastic SIEM, you can use the below detection logic to aid in the detection of adversary activity within your environment. Additionally, the provided defensive recommendations may be used to harden and defend vulnerable systems from the successful exploitation of this campaign.
Use the following detection in Elastic to identify this cluster of activity (ProxyShell):
- Existing logic:
- New logic:
[/et_pb_text][et_pb_divider _builder_version=”4.14.2″ _module_preset=”default” hover_enabled=”0″ sticky_enabled=”0″][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”4.14.2″ _module_preset=”default” min_height=”433.6px” custom_margin=”-48px|auto|-107px|auto||” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.14.2″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.14.2″ _module_preset=”default” min_height=”285.6px” custom_padding=”||0px|||” global_colors_info=”{}”]
Red Team Operations
Antivirus Bypass Techniques with Python
In this post, we discuss how to reveal which antivirus software is installed on an endpoint by using a WMI process enumeration technique and look at the importance of adapting your antivirus bypass techniques to specific antivirus software. There are innumerable ways to implement a red team operation that includes antivirus software fingerprinting and antivirus bypass. But let’s first discuss the difference between a pentest and red teaming.
Pentest vs. Red teaming In a penetration test, practical exploitation followed by Proof of Concept (PoC) proves that an organization is vulnerable, and thus its integrity and information security can be impacted. At the end of a penetration test, a report must be written that will include each of the found vulnerabilities, prioritized by its relevant risk severity, and then sent to the client.
In a red team, the goal is different—when a company wants to conduct a red team operation, the company will want to know whether they could be exposed to intrusions, whether this is through a vulnerability found in one of their publicly exposed servers, through social engineering attacks, or even as a result of a security breach by someone impersonating a third-party provider.
Fingerprinting antivirus software
Antivirus fingerprinting is a process of searching and identifying antivirus software in a target endpoint based on identifiable constants, such as the following:
- Service names
- Process names
- Domain names
- Registry keys
- Filesystem artifacts
The following table will help you perform fingerprinting of antivirus software on the endpoint by the service and process names of the antivirus software:

Note: The content in this article is based on the title Antivirus Bypass Techniques published by Packt.
You do not have to rely only on process and service names—you can also rely on registry names, and more. We recommend that you visit the Antivirus-Artifacts project at https://github.com/D3VI5H4/Antivirus-Artifacts to find out more about this.
You can perform fingerprinting on a simple Python script, for instance, which will monitor all processes running on the operating system and compare predetermined strings. For example, let’s look at the following simple code:

As you can see, using the preceding Python code, you can determine which antivirus software is actually running on a victim endpoint by utilizing Windows Management Instrumentation (WMI). With this knowledge of which antivirus software is actually deployed in the targeted victim endpoint, as well as knowledge of the gathered research leads, you can then download the next-stage malware that is already implemented with our antivirus bypass and anti-analysis techniques.
To compile this script, you can use pyinstaller with the following command:
pyinstaller –onefile “Antivirus Fingerprinting.py”
You can see that the script detects the Microsoft Defender antivirus software on the endpoint by its process name:

In the following screenshot, you can see the results from VirusTotal, which show that in fact, six different antivirus engines detected our legitimate software as malicious:

VirusTotal’s detection rate of 6/64 antivirus engines
The name of the signatures that triggered the detections in each one of these antivirus engines are:
Trojan.PWS.Agent!m7rD4I82OUMTrojan:Win32/Wacatac.B!mlTrojan.Disco.Script.104
These detections are, in fact, false positives.
It is important to understand that the detection rate in each uploaded sample in VirusTotal changes after clicking on the Reanalyze file button. In the following screenshot, you can see the same file, after almost 3 months since the first submission:

VirusTotal’s detection rate of 1/64 antivirus engines
Tip: After writing antivirus bypass custom-made code and being sure that the antivirus software detects it as a false positive, try to wait some time and you will most likely see a drop in the detection rate.
Many malware authors and threat actors use this technique to identify which antivirus software is installed on the victim endpoint in order to apply the relevant bypass technique.
Disclaimer: Ensure you only conduct red team operations or pentest systems and networks that you own or have legal permissions to do so.
Special thanks to Nir Yehoshua and Uriel Kosayev
Recent Security Issues
LockBit 2.0 targets organizations across the globe
The ransomware-as-a-service network behind the LockBit ransomware is launching new attacks using the 2.0 version of its malware. LockBit has recently been spotted targeting organizations in the U.K., Taiwan, Chile, and Italy. This new version of LockBit includes new encryption features and an effort to recruit “insiders” at the targeted organizations. Once the malware encrypts the data on the targeted machine, it changes the wallpaper to display an advertisement, telling users that they can become a part of LockBit’s recruitment process, promising payouts in the millions of dollars. LockBit’s been behind several recent high-profile attacks, including one on Accenture. Read more.
Cloudflare: Massive DDoS Attack
Cloudflare reported that in July, it detected and mitigated a distributed denial-of-service (DDoS) attack that maxed out at 17.2 million HTTP requests-per-second. The attack lasted less than a minute. Cloudflare says the attack was using more than 20,000 infected devices in more than 100 countries. The same botnet targeted a different Cloudflare customer last week with a maximum rate of eight million requests per second. Read the blog.
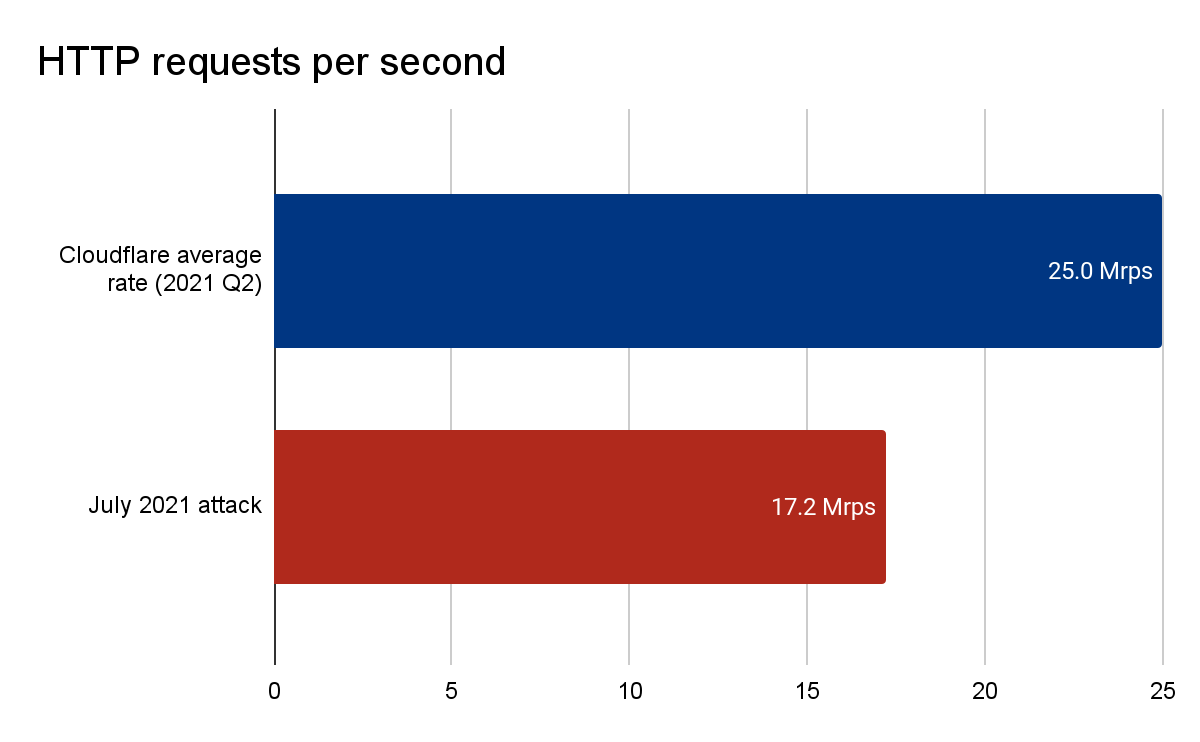
Comparison graph of Cloudflare’s average request per second rate versus the DDoS attack
Secret Knowledge
Discover useful security resources, cheatsheets, hacks, one-liners, and open-source CLI/web tools.
Network
- mylg – utility which combines the functions of the different network probes in one diagnostic tool.
- netcat – utility which reads and writes data across network connections, using the TCP/IP protocol.
- socat – utility which transfers data between two objects.
- tcpdump – is a powerful command-line packet analyzer.
- tshark – is a tool that allows us to dump and analyze network traffic (wireshark cli).
GUI Network Tools
- Wireshark – is the world’s foremost and widely-used network protocol analyzer.
- Ettercap – is a comprehensive network monitor tool.
- EtherApe – is a graphical network monitoring solution.
- Packet Sender – is a networking utility for packet generation and built-in UDP/TCP/SSL client and servers.
- Ostinato – is a packet crafter and traffic generator.
Encoders/Decoders and Regex testing
- URL Encode/Decode – tool from above to either encode or decode a string of text.
- Uncoder – the online translator for search queries on log data.
- Regex101 – online regex tester and debugger: PHP, PCRE, Python, Golang and JavaScript.
- RegExr – online tool to learn, build, & test Regular Expressions (RegEx / RegExp).
- RegEx Testing – online regex testing tool.
CVE/Exploits databases
- 0day.today – exploits market provides you the possibility to buy/sell zero-day exploits.
- sploitus – the exploit and tools database.
- cxsecurity – free vulnerability database.
- Vulncode-DB – is a database for vulnerabilities and their corresponding source code if available.
- CVE Mitre – list of publicly known cybersecurity vulnerabilities.
Other Resources
Inside Figma: securing internal web apps
Figma’s Security Engineer Max Burkhardt describes their system to securely provide access to internal apps using AWS ALBs, Cognito, Okta, and Lambda.

Okta: The State of Zero Trust Security 2021 Report
Use this report to learn how organizations around the world are approaching Zero Trust today and where they’re headed over the next 12-18 months. Note this is gated content.
Modern SecOps with Zscaler and Sumo Logic
Sumo Logic has released separate apps for Zscaler Internet Access and Zscaler Private Access.
Osquery: What it is, how it works, and how to use it
Mark Knowles of Uptycs discusses how to get started with Osquery, build vs. buy, and how to run Osquery at scale in this detailed post. There’s also a presentation video at osquery@scale by Zachary Wasserman who explains the depth of thought and effort that managing Osquery performance requires.
The Puzzle Section
Check your knowledge. Select the correct response to the following questions:
1) What kind of exercises can be performed to simulate attack scenarios that are difficult or challenging to do during real-world cyber-operational red teaming?
2) Azure Sentinel stores data in…
A. Azure Storage
B. Azure SQL Database
C. A Log Analytics workspace
*Clue: Answers are placed at the end of the newsletter.
Answers
1) Tabletop exercises can be performed to simulate attack scenarios that are difficult or challenging to do during real-world cyber operation red teaming.
2) C. A Log Analytics workspace
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes.








