Security Service Edge (SSE)
Written By: Andy Pantelli
Traditional Security Platforms dominated by on-premises solutions should now be considered unfit for purpose and consigned to the history books as ‘legacy networks in a bygone age’. Bold Statement you ask? Not really, just realism. The Enterprise transition to the Cloud is moving at pace, and faster than predicted. This has left many organisations reliant upon infrastructure build upon outdated concepts & designs based around the physical Data Center.
The Covid Pandemic not only has changed the traditional workplace from the Office to that of one being anywhere we choose to be with an internet connection. Let’s leave the whole WFH debate for another time but the point being that the workplace has changed, and that Enterprises must also change their ways of working. Applications have moved into the Cloud, and with that Security frameworks & models must follow. Organisations that do not embrace this change will face increasing risk. Enter SASE or Secure Access Service Edge to give it the full title. This Security Architecture provides a framework for Cloud based solutions that provide the protection Enterprises need. This article will take a look at SSE (Security Service Edge), a fundamental set of Security services part of SASE. This subset provides the capabilities to implement the Security services required to protect Remote Workers, Cloud infrastructure and even existing on-premises applications. Simply put SASE provides the framework with SSE providing some of the services required.
Digital transformation is enabling businesses to innovate faster with a Cloud based Security posture. Security in today’s world needs to be smarter, not just better. Increased attack vectors with more sophisticated adversaries means that Security must be enhanced using new techniques. Context awareness providing users protection wherever they are connecting from, on whatever device, using any Platform. SASE is facing a challenge in transforming the hybrid workplace. Legacy security products or services cannot fit into the Cloud model, nor will trying to relabel old technologies as ‘Cloud enabled’. Instead, new offerings of Cloud native solutions where Data and applications are on infrastructure that the Enterprise does not directly control. How do we as Security Professionals enable our organisations to adapt, & evolve? Before looking at how, we should understand why Security Professionals, Engineers & Architects should change their culture and introduce the new world into their organisations.
Cloud Computing offers business value and flexibility. The Cloud is becoming more appealing to C-Suite leaders and to the business in general. It’s faster, more cost effective and offers better integrations with partner platforms & third-party applications. The challenge to fully embrace and adopt to a Cloud based environment is of IT teams relinquishing control over infrastructure and applications. Cloud applications are not controlled, nor managed by the organisation and there lies the difficulty in accepting the change. Cloud Access Security Brokers (CASB), and Secure Web Gateways (SWG), Zero Trust Network Access (ZTNA) were early Cloud Security tools, but these again lacked full integration. How then, do we change our culture and our Security models?
TRANSFORM
Networks are simply moving data from A to B. Getting the packet from source to destination. We must do this efficiently though, and of course securely. Cloud based architectures are optimised to support SSE by having globally distributed points of presence (POPs). Wherever the user is connected in today’s modern world and hybrid working the experience is high level security and performance.
CONSOLIDATATION
Adapting to a unified, single vendor approach offering a suite of extensive SSE replacing multiple security technologies. Merging functionality simplifies management & administration.
ADVANCED SECURITY SERVICES
SSE provides a range of powerful capabilities, such as Remote Browser Isolation (RBI), Cloud Security Posture Management (CSPM), SaaS Security Posture Management (SSPM) , Advanced Threat Protection (ATP), and Data Loss Prevention (DLP). Some of which legacy systems offered had limited visibility and inefficient integration
CLOUD DATA PROTECTION
Firewall as a Service (FWaaS) should be offered by the SSE Vendor to protect Cloud based applications.
RETHINK THE DATA CENTER
Legacy Architecture placed the Data Center at the Central point in the Network. Inefficient traffic back-hauling, or hair-pinning is replaced with SSE with the Data Center becoming just another destination routing traffic to, and from. Reducing cost & complexity thereby increasing performance.
ZERO TRUST
SSE provides contextual monitoring of traffic after access is granted, leveraging third-party integrations that provide threat intelligence and detecting any changes in the network dynamically.
REDUCE RISK
Enhanced visibility greatly improves awareness, detection & monitoring of risks. The adage that we can’t protect what we don’t know about is extended by giving Security Teams more time to look at critical, high value assets with that added enhanced visibility.
WHY WE NEED SSE
Driving the need for SSE is the understanding, and realisation that our legacy Perimeter based approach is no longer fit for purpose. By defining and making use of SSE architectures we incorporate the old with the new, that is to say Identity and Access Management are still relevant and controlled, but we introduce alongside the Zero Trust principles to grant access based on attributes of the entity and the level of access which will be granted. The risk of using the Implicit trust model where compromised Servers could potentially allow for lateral movement unrestricted based on the same security principle model within the ‘Trusted Zone’ is mitigated using the ‘trust but verify’ construct. Minimum access and context based on identity, device identity, role-based access control, location and data classification are some of the techniques used. Effectively using a ‘Single Pass’ methodology security services mentioned earlier work in parallel, simultaneously in real time.
DIGITAL TRANSFORMATION
To achieve this, we must first have at least a high-level understanding of the ‘Cloud’. Cloud offers the Enterprise scalability and flexibility, reducing infrastructure costs whilst optimising services. SaaS applications allow our users to get the same level of access & experience regardless of where they are located. Moving away from legacy designs and constructs presents Administrators with a concern that they no longer control their environments.
Relinquishing this control is the biggest challenge thus far in convincing C Suite Officers into moving away from on-prem infrastructure. Another concern is how we secure the ‘Cloud’ when we can’t say that we control it. Whilst SASE is the overarching framework to transition Networking & Security to the Cloud, SSE aims to achieve this by securing Web, Cloud and locally hosted applications, in doing so safe and reliable access to applications will be provided following Zero & Adaptive Trust Principles.
By providing the components into a single construct to simplify management and reduce overhead SSE is the orchestrator of security services including Data Loss Prevention (DLP), Advanced Threat Prevention (ATP), Cloud Security Posture Management (CSPM), SaaS Security Posture Management (SSPM), Content Access Security Broker (CASB), Secure Web Gateway (SWG), Zero Trust Network Access (ZNTA), and Digital Experience Management (DEM) Remote Browser Isolation (RBI), Firewall as a Service (FWaaS), End Point Protection (EPP), User Entity Behavioural Analytics (UEBA). Working intelligently, and collaboratively a unified solution provides cohesion and interaction within a single Platform.
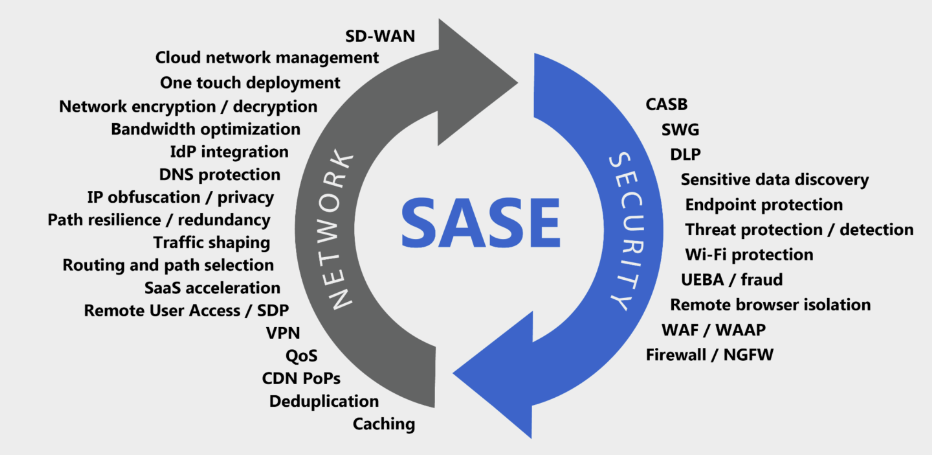
Security in the Cloud is not the only consideration. How we design, configure, deploy and consume our Networks will also undergo a radical transformation. Access must be distributed to allow our rapidly shifting workforce to benefit from cloud-based architectures and SSE. Legacy designs where Branch offices had to connect back into a central Data Center and relying upon protection at the Perimeter is difficult to scale, manage and inherently costly resulting in inefficient and ineffective controls.
The Cloud based approach is based on an architecture designed for Remote Workers, allowing connectivity from anywhere, at any time. This is both scalable and manageable, by peering with providers whose backbone network can provide numerous direct connections in virtually any destination. This level of provider can offer better performance, resilience and a more consistent, reliable connection. This the core concept of SASE, the transformation of both the Security, and Networking stack to provide a modern, & reliable framework.
ZERO TRUST
From a point in time five years ago we are now seeing a rapid adoption of the Cloud but to continue this acceleration and move away from On-premises & Data Center design the security and business benefits must be communicated. To do this, we must fully understand the Zero Trust methodology. Legacy architecture was reliant upon the construct of a rigid policy of ‘Allow’ or ‘Block’, ‘Permit’ or ‘Deny’, literally all or nothing. We now move to a shift in construct with the concept of adaptive trust being used within the Zero Trust paradigm utilising several attributes, or conditions with identity being a factor along with other criteria such as location, device, the type of network connection and many more. This granularity gives us the extended visibility and control which we discussed in an earlier chapter. This adaptive trust model is demonstrated by the context in which an application is being used. This can change from a secured TLS connection when using a business app or shifting in scope when a personal email is read from healthcare organisation, or by accessing a personal banking application. In which use case decrypting the traffic flow would be in breach of individuals right to privacy or regional regulations such as GPDR. The Zero Trust model is extended with Zero Trust Network Access which gives the organisation the control over Remote User access which was lacking in legacy VPN solutions which gave all, or nothing. With our ZTNA component of SSE within a SASE construct access is controlled to parts of the Network, or by application that is being granted, without the ‘all or nothing’ model.
Zero Trust is a relatively new paradigm, and as such is constantly evolving but based on the premise that defences are being moved away from static perimeter-based security to a model which focuses on users, assets and resources. Some of the key components include; CONTEXT – by making use of attributes the context of access can be defined. LEAST PRIVILIGE – the concept of least privilege based around ‘never trust, always verify’. POLICY ENGINE – (PE) used to grant, revoke or deny users to specific enterprise resources. POLICY ENFORCEMENT POINT (PEP) enables, terminates and can monitor connections between a user and Enterprise resources. RISK SCORING – using UEBA techniques building a baseline of expected behaviour
1NIST define Zero Trust as “Zero Trust is not a single architecture but a set of guiding principles for workflow, system design and operations that can be used to improve the security posture of any classification or sensitivity level”
MIGRATING TO SSE
For many organisations the most important aspect of embracing SSE within a SASE paradigm is to move towards a Cloud based operating model and move away from On-prem architecture. In moving away from securing the Enterprise at the perimeter this becomes the starting point for most organisations.
To begin, understanding the workforce operating practices to help identify just where users are connecting in from. It may be the organisation is stuck in pre pandemic mode and enforcing the workforce to travel into the office or branch locations daily, or perhaps the business just simply cannot provide their employees the option to work remotely for operational reasons. Whichever the case may be, it’s the first step to understand how to migrate to SSE. Next is directing web traffic to a Secure Web Gateway (SWG), and their SaaS traffic via Cloud Access Content Broker (CASB). This should provide the Enterprise visibility into user traffic and application behaviour.
Next would be migrating the Data Center VPNs to SSE Zero Trust Network Access which improves security and the user experience in one process. This controls access to only the required applications and prevents Remote Users from being given access to all East West resources based on the legacy ‘Permit’ or ‘Deny’ concept which was by definition an ‘all or nothing’ solution. After this point we would leverage SDWAN being the Network connectivity aspect of SASE to connect users via the Providers closest Point of Presence (PoP).
By now the migration should give the enterprise admins a greater understanding of data, applications, web browsing behaviours, and other services which the workforce are consuming. This underlies the power of SSE in which we described the enhanced visibility in an earlier chapter, which in turns gives us the context to make the adaptive trust which is a core component of SASE and ZTNA architecture.
With this visibility the organisation can look to achieve greater security being able to classify applications, data and entities based upon risk and behaviour. Continuous adaptive trust can evaluate behaviour and context to evaluate risk to provide the correct access defined in security policies which are intelligently written based on evidential data. With SSE data classification can assist Security Professionals which data is sensitive and which applications or web sites should be considered as risky giving greater control and reducing the risk of DLP. In the final stage of a migration, by using UEBA to score risk and behaviours of users, entities, applications & devices.
This can assist with the early identification of suspect behaviour in the network such as privilege escalation. Using Digital Experience Management (DEM) & Cloud Security Posture Management (CSPM) further increases risk management.
SUMMARY
Gartner predict that by 2024 around 40% of Enterprises will have, or be looking to have adopted SASE. Implementing SSE is a fundamental aspect of SASE and not optional. SASE not only reduces network complexity but greatly enhances the security posture whilst reducing IT admin overhead. No doubt, as we said in the opening chapter of this article that legacy networks and architectures are outdated and will eventually be consigned to the history books, this will take out the traditional concept of the Enterprise Data Center and On-Prem solutions.
In doing so the role of the Security Professional, and indeed the Network Professional will also be fundamentally shifted. To embrace change and to adapt is to evolve and in doing so to survive. As history has shown, and no doubt be repeated those that stand still, or fail to adapt get left behind, although this isn’t the time to disown the Data Center. It is a change of how we work that is required not a complete reinvention of the wheel.
The Data Center will remain, after all the Cloud is simply ‘someone else’s tin’. At this time, as with all cutting-edge technology implementing SASE and with it SSE is only affordable to the large organisations and Enterprises with the budgets capable of affording the cost. In time eventually SSE will become mainstream and adopted by organisations both large and small with research showing that by 2027 the Secure Access Service Edge Market size is expected to reach $5.7 billion.2 For Security Professionals looking to protect their organisations not just for today, but for the long term SASE, and within it SSE, will become the de facto framework to adopt with the Perimeter based Security model as we said earlier, left in a bygone age.
ACKNOWLEDGMENTS & REFERENCES
Any content or copyrighted material referenced is acknowledged to be the property of the respective owner.
- NIST Special Publication 800-207 Zero Trust Architecture (nist.gov)








