SunCrypt Ransomware – an Analysis of a Surprisingly Simple RaaS
Written By: Austin Miller
After first emerging in 2019, we saw SunCrypt rise from the ashes in 2020, 2021, and, as of last month, again in 2022. As far as ransomware-as-a-service (RaaS) providers go, the team behind SunCrypt seem to be dead set on developing a piece of malware that is constantly reinventing itself and providing illicit value to the cybercriminals of the world.
As you can expect, the minor changes made in the ransomware have made it difficult for security researchers to keep up with an effective analysis of the malware. For that reason, here is a breakdown of the latest version of SunCrypt that the SecPro team has been able to identify. As always, some advice on how to avoid falling victim to this RaaS is included at the end.
What is SunCrypt?
SunCrypt has been around since the late 2010s and was a world leader – if we want to phrase it that way – in “triple extortion”, a technique that has been copied by many ransomware gangs in recent years. By combining encryption of files, exfiltration for extortion, and distributed denial of service (DDoS), the SunCrypt team created a piece of malware that placed the cards firmly in the hands of the adversary.
Yet SunCrypt has not become a threat that keeps security professionals up at night like Conti, WannaCry, or REvil. Even though the team has no problem leasing out their malware to people wanting to shut down schools or hospitals, it hasn’t grown in popularity to the level of the most fearsome ransomware examples that give us all cold sweats. Instead, it has developed a seemingly loyal (if somewhat small) circle of subscribers that always come back.
Somewhat interestingly, the SunCrypt ransomware is associated
How does SunCrypt work?
As to be expected of a ransomware gang who are focusing on their “product” professionally, SunCrypt has a multi-stage, multi-prong approach to extorting victims.
Initial Infection
SunCrypt (sometimes referred to as Ransom.SunCrypt) is spread in the form of a .dll file that is implanted via a PowerShell script. It is suspected that the team is also working with other hacking groups such as Trickbot, with the Trojan virus specialists acting as initial access brokers (IAB).
Loading
Despite being a relatively simple and possibly underdeveloped piece of ransomware, SunCrypt still uses a multi-pronged attack procedure to lock down victims.
After initial infection, stops the system from recognising critical-error-handler errors by editing SetErrorMode (0x1 = SEM_FAILCRITICALERRORS).
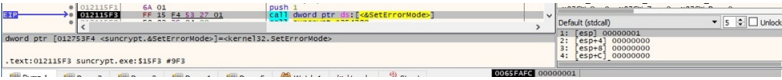
The .dll also calls the LoadLibraryA API, downloading the following malicious files:
- ntdll.dll
- advapi32.dll
- kernel32.dll
- rstrtmgr.dll
After using various calls and strings to attain privileges, SunCrypt starts to use living of the land (LotL) techniques to investigate the machine. For example, GetSystemInfo and RtlGetVersion is used to retrieve information about the machine and then the malware creates a mutex to stop multiple instances running at the same time.
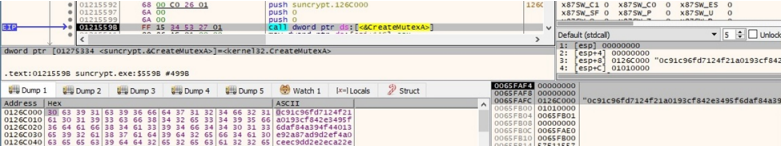
SunCrypt then kills a large number of processes – including ocssd, dbsnmp, firefox, and powerpnt, but also a few odd inclusions such as steam – duplicates a new access token through the DuplicateTokenEx API, and impersonates a token on the system by calling SetThreadToken.
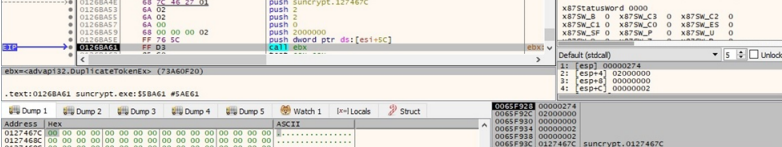
Encryption
From this point, SunCrypt deletes all Volume Shadow copies and starts to encrypt the files, using a created I/O completion port.
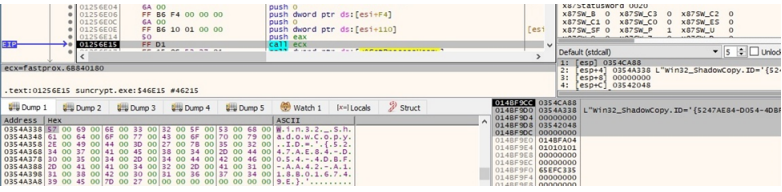
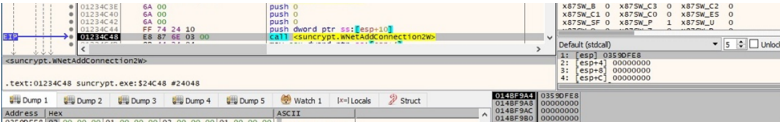
As this happens, the malware makes contact with a network share via the WNetAddConnection2W routine, creating a copy of all files as they are encrypted.
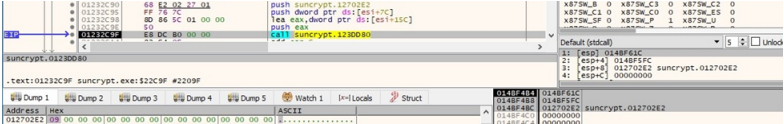
Key Creation
After creating 32 random bytes to act as a buffer, a 32-byte secret key is created.
From this point, the system is encrypted and the adversary can begin to extort the victim. How are they going to do that? With an ominous telephone message recording and ransom note, of course!
The Ransom Note
What’s a ransomware gang without an ominous ransom note?
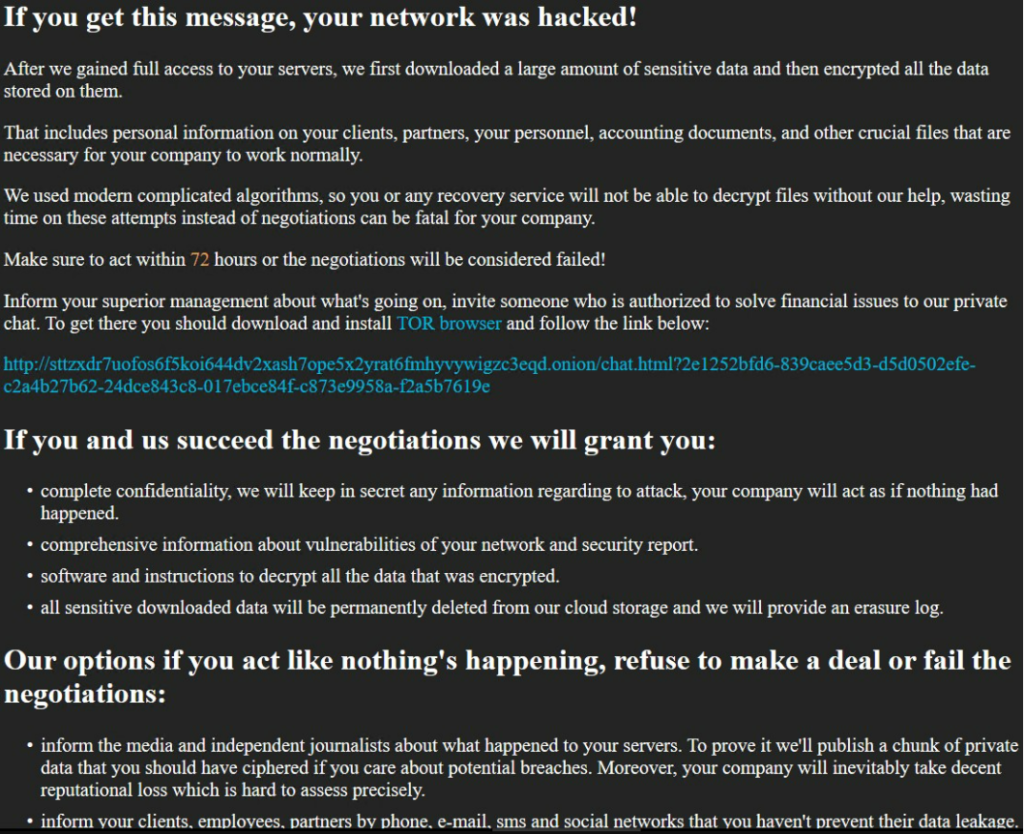
As clearly stated in the note, the team expects negotiations to happen over a TOR chat. No definitive plans for payment are declared, but as seen in the New Jersey hospital case, payments are in the high hundreds of thousands.
As noted by other security researchers, it seems like SunCrypt – despite being on the market since 2019 – is under development and changing.
How can I defend my organization against SunCrypt?
As always, the best form of defense against ransomware is to close the vector that allows the malware into your system. As SunCrypt relies on a PowerShell script, this is somewhat difficult – stopping PowerShell from working would be debilitating for most IT teams around the world, so a more nuanced approach is necessary.
For a full breakdown, consult the MITRE ATT&CK Top 10 techniques on T1468 – Data Encrypted for Impact. Here, you will find out more about how the adversary uses various techniques to encrypt a system and the mitigations that MITRE recommends for overcoming the threat of ransomware lockdown.
Indicators of Compromise: