In part 1, we explored some of Wireshark’s options for security analysis and information extraction from network traffic captures. In this article, we will discuss other methods to extract information from packet captures.
Packet filters
We know that there are two filters: capture Filters and display filters. Let’s see how analysts can leverage them to narrow down the capture packet noise and clear it. We use Capture Filters to filter, in a predefined manner, and to view only particular criteria of traffic.
Syntax of Capture Filter
- Type: Used to select the type of traffic like Host, Network, protocol, and Port range.
- Dir (Direction): Dir is used to specify the inward or outward direction.
- Proto (Protocol): Proto specifies the possible protocol combinations, whether its TCP or UPD, along with the port number.
Display filters
The display filter is like a search engine in the PCAP file. It helps us to filter out packets and shows us the traffic as per the query. It supports all interfaces, ports and protocols. Additionally, Wireshark provides us a larger variety of filters for advanced analyses like creating macros in display filters and adding predefined expressions to the display filter, specifying vendors, IEEE standard devices, and so on.
These can be explored under Display Filter Macros and Display Filter Expressions.
How to Use Filters
The analyst can start with the type of packet that is required to filter first, for example IP, HTTP, or TCP. Once it is typed into the program, Wireshark will show autofill combinations of filtered links to extend the filter. Wireshark also provides the colouring of the display filter for both successful and unsuccessful syntax so that analysts can review the filter.
Additionally, in case of a roadblock, analysts can use the “Display Filter Expressions” GUI tab to create the query and insert it in the search box. Analysts can create custom queries within the scope and add them to the list for future reference.
Using Statistics
The Statistics menu provides multiple statistics for analysts to investigate and connect the dots in terms of the range of the traffic, available protocols, hosts and communications, and some transport layer details like DHCP, DNS, and HTTP/2.
For any investigation, a handful of basic information is required like IP address, Port, Protocol, and traffic details. You can use the “Statistics” menu to view all available options.
Capture File Properties
This gives us the complete summary of the PCAP file. It shows us details of File, Hash, Network, Packet, and Packet comments.
Resolved Addresses
This feature helps analysts access a list of all the resolved hosts in one place. This will help analysts to connect the dots and identify if any malicious domain or IP has any communication within or outside the network. This tab also captures all the port details, which can help to understand which services have been used so far.
Protocol Hierarchy
This option gives a summary of all the protocols and their subsets from the capture file and helps analysts view the protocols in a hierarchy based on packet counts and percentages. Thus, analysts can view the overall usage of the ports and services.
Analysts can also export all the data in CSV or YAML form. This feature doesn’t have a display filter.
Conversations
This menu helps to view all device communications at once on a single tab. It includes Device-, IP-, Port-, and Protocol-level Communications. These data can be exported in CSV and YAML.
Endpoints
This tab shows the list of endpoints along with the packets from the traffic. This tab shows Interface, IP, port and protocol. Wireshark supports resolving MAC addresses to human-readable format using the manufacturer name assigned by IEEE.
Configuration Profiles
Wireshark is an advanced tool that helps analysts to accomplish in-depth packet analysis. Wireshark provides configuration profile templates that can be used by different roles in the security domain. Some can be used for the security operations, VAPT, and Admin teams. You can use the Edit to Configuration Profiles menu to create, modify and change the profile configuration. It also allows users to import pre-configured profiles to make the task easier for other analysts.
Let’s look at some of the common attack workflows which can be investigated using Wireshark Captures.
Decrypting HTTPS Traffic Using Wireshark
During Web application activity analysis, analysts often run across encrypted TLS/SSL traffic. HTTPS uses TLS protocol to encrypt communications, for enhanced security. It is impossible to decrypt the traffic and view the transferred data without having the encryption/decryption key pairs.
Similar to the TCP three-way handshake process, the TLS protocol has its handshake process.
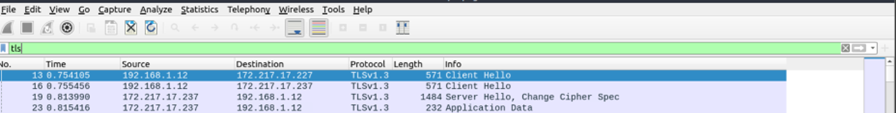
The first two steps contain “Client Hello” and “Server Hello” messages. The final Step is Authentication.
This is how secured communication starts when TLS is enabled. We can also filter the packets based on the display filters.
- Client Hello: (http.request or tls.handshake.type == 1)
- Server Hello:(http.request or tls.handshake.type == 2)
Now let’s see the HTTPS traffic to understand how TLS works. As this is encrypted traffic, we cannot view the traffic without the decryption traffic, which makes it more secure. These key pairs are generated during the connection establishment.
Once we import the keypair into the tool, we can decrypt the captured traffic. This will give us additional information about the traffic. Depending on the packet details, you could have additional details like Decrypted TLS, TCP Reestablishment, and Reassembled SSL.
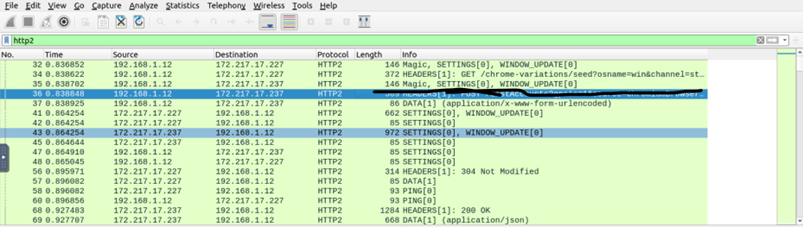
Once you’ve done this, you get access to encrypted data. It’s easy to decrypt sensitive information. This also applies to other actions such as sniffing the clear text credentials attack, sensitive information transfer attack, and multiple other web-based attacks.
Thanks for that article, Sai. It’s always useful to look back on the day-to-day tools that help us do our jobs. Wireshark has always been a personal favorite, so it’s been great reflecting on how the tool is used. Now, onto the next article – this time, looking at another piece of malware where Wireshark might not actually help you all that much.








