Post Credit: Ricoh Danielson
Threat Hunting Within O365
Security operations and incident response teams need to be constantly on the lookout for new threats. Moreover, you need to be able to identify the specific activity spanning thousands of endpoints, the interconnections between the various log sources and how this information can be used to react and respond appropriately.
Today’s security operations teams need tools that make it easy to spot out of the norm activity. Detecting out-of-the-ordinary behavior as quickly as possible is the challenge for security operations centers (SOCs). That’s very challenging!
Let’s face it, all security teams want to stay ahead in their game. We help them gain visibility into their environment and find threats that are causing issues before they are a problem. Put your mind at ease. Whether you have a small team or thousands of users, we’ll provide you with the information you need.
Threat Hunting Within O365: In 0365, performing an advance threat hunt is a critical part of securing the system.
The majority of the world has migrated to 0365 or a hybrid version of 0365. Threats can, therefore, be hunted and mitigated within the 0365 environment and settings.
Most businesses either have the expertise of how to mitigate these threats in-house or utilise a third-party source like an MSSP.
In any case, more research into how, why, and what to look for in these data elements can greatly help us mitigate these threats. What we’re looking for is a magical question. So, the first step to hunting for security incidents is to know what to look for.
What is required to conduct threat hunting in 0365?
To run threat hunting in 0365, the technical researcher will need access to an instance of 0365. Depending upon how it is configured, there might be different viewpoints; however, here’s an example of a fully set up dashboard.
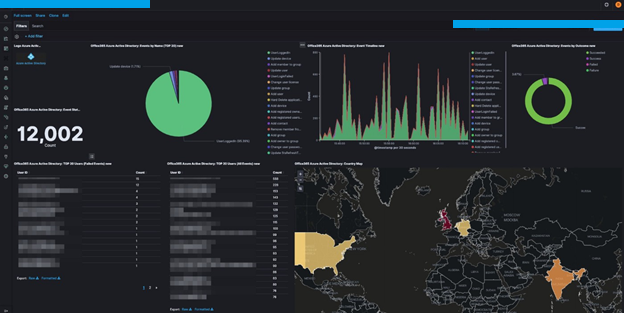
We can see that we have several indicators from pre-designated tags that would enable us to see trends. Also, we can determine what countries at the store doctors are supposedly coming from. Essentially, understanding this at this level of research is critical since these signs are vital to watch for during an incident, allowing us to take proactive measures.
The cyber security researcher who does not have this cool looking dashboard will give them a sense of true North. This is where you’re going to have to roll up your sleeves and jump into the metadata and understand where, how, why, and more specifically, who is knocking at your door. We do this by manually researching.
Why do we value manual processes over tools if they might be better at achieving our goals?
The next step would be to comprehend the benefits of a manual approach. There may be a requirement to execute some queries during an incident or an active threat. The sting below would allow for the detection of some of the most commonly utilized Power Shell .exe by threat actors. Using this strong can reveal a route, a unique file name produced by threat actors, and a C2 domain that is being called back. All of these assets and data points are crucial to comprehend the strategies. Then I’ll share more commonalities, as well as Datapoints that lead to a specific threat actor.
// Finds PowerShell execution events that could involve a download union DeviceProcessEvents, DeviceNetworkEvents
| where Timestamp > ago(7d)
// Pivoting on PowerShell processes
| where FileName in~ (“powershell.exe”, “powershell_ise.exe”)
// Suspicious commands
| where ProcessCommandLine has_any(
“WebClient”,
“DownloadFile”,
“DownloadData”,
“DownloadString”,
“WebRequest”,
“Shellcode”,
“http”,
“https”
)
| project Timestamp, DeviceName, InitiatingProcessFileName, InitiatingProcessCommandLine, FileName, ProcessCommandLine, RemoteIP, RemoteUrl, RemotePort, RemoteIPType
| top 100 by Timestamp
Identifying and analyzing findings of a live Threat Hunting Within O365
We can begin the analysis and forensics discovery now that we have a manual starting point and a few query strings to obtain vital data. Various data items can be obtained during the analysis phase, which may or may not result in information fidelity inside the IOCs. We may come across certain domains when extracting these crucial data points for IOC that will supply you with a large amount of state-of-the-art knowledge.
Find them, Fix them and Flush them out.
There’s a terminology that we use in the military. It’s called find them, fix them and flush them out. This is where we’re actively threat hunting to find the threat actor in the environment. First, we need to find them, and how we see them is by the IOCs. Fix them; in this phase, you get a target acquisition on threat actors and get a good fit. This could be an account, advice, or a specific network. The last part is to flush them out; flushing the threat actor out uses different defensive skill sets and techniques to ensure they cannot obtain the access they need to carry out further attacks. As we apply these contain methods, it will allow us to move ahead of the threat actor. Something else to consider is the embedded items in the URLs called out. Overlaying this with a network forensics tool or aggregate logs to determine the value can show how and when they connect to the network. Once we can find a network connection, it would be an idea to close down these ports, services, and ranges. Granted, when it comes to network isolation, there needs to be a business consideration that removing the device may cause a business impact.
| hXXps://www[.]lagesports[.]com/[.]tmb/xml[.]php | 69[.]10[.]32[.]186 |
| hXXps://rtoutletpremium[.]com[.]br/[.]well-known/pki-validation/UTR/index[.]php | 162[.]241[.]182[.]5 |
Conclusion
In closing, whether you use 0365 tools, which is highly encouraged, or if you need to make threat hunting the old way, some threat hunting is better than no hunting. Threat hunting in 0365 is a requirement for doing business; if not, the threat actor will have a field day in your environment. The great lesson here is that 0365 hunting can narrow down the search for the threat actor. Still, you may need to actively engage local technology combative to remove the threat actor out of your environment.
A truly effective threat hunter needs to think like a criminal hacker. They need to know what to look for, and how to find it. Plus, they need to be well-versed in the latest tools and technologies that hackers rely on. Thus, a threat hunter should also be well-versed in domain knowledge which includes system/network administration, application security, development methodologies and practices, encryption implementations and binary code analysis amongst other things. Basically, threat hunting takes a deep dive into organizational processes and IT systems looking for any anomalies on servers or any unassigned geo-location traffic from mobile devices.
Threat hunting is an essential part of any cybersecurity strategy today, and it’s only going to become more and more important in the years to come. Be sure to explore your options, consider all available resources, but most importantly, don’t wait! Your security team will always be able to use additional help improving your overall network defense posture.
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes. Join the newsletter here.








