Post Credit: Austin Miller
The world of cybersecurity is difficult to navigate and confusing for beginners, so understanding the basics and giving practical advice about how to implement them is a high priority for SecPro. This week, we’re going to explore how threat modelling helps new security analysts support the development process.
To help new cybersecurity professionals make their way in the world, the SecPro team will be launching the Beginner’s Corner as a fortnightly feature. Keep your eyes open to catch some important tips.
Threat modeling for beginners
Although there is little technical know-how involved in threat modelling, it is key to understand how to identify threats, implement security controls, and reduce risk wherever possible. That’s why we’re going to start our [feature title] with the most fundamental skill of all – threat modelling.
Threat analysis will always be a large part of any risk management methodology, but understanding how to turn knowledge about various security issues into workable solutions is… [MORE]
Understanding your role
Not everyone who is threat modelling is a security professional. In fact, you should expect software developers to have similar concerns about threat agents throughout the Software Development Life Cycle (SDLC). Because of that, you need to understand the differences between a developer’s threat model and your version as a security professional.
Here is how a software developer will look at security requirements throughout the SDLC:
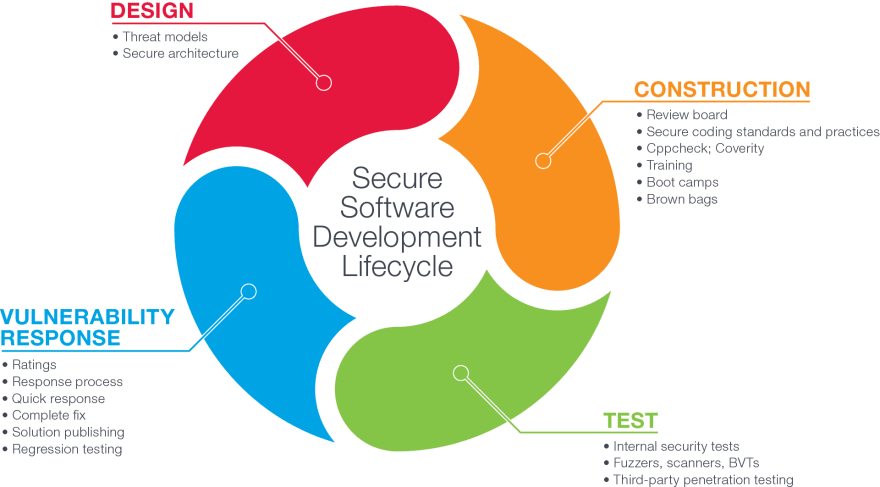
Threat models are included within the SDLC, but they are only the starting point. Source
Whereas your threat modelling process should look a little more like this:
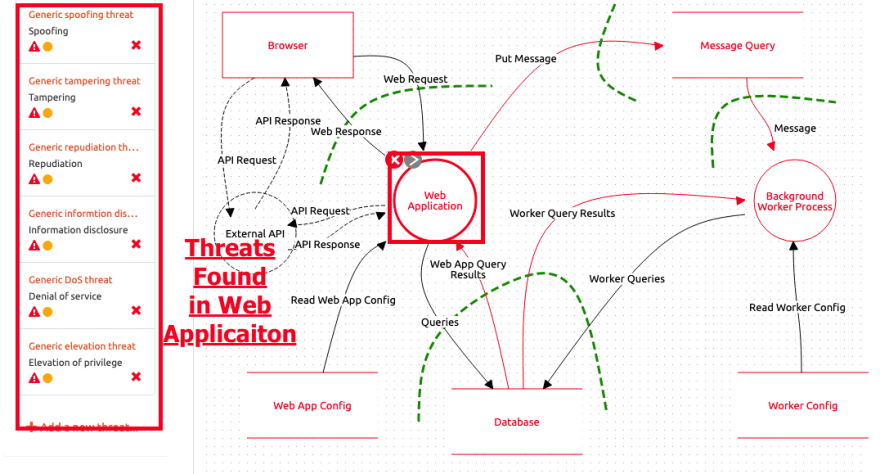
Although this threat model is very busy, it shows us exactly where the security professional has identified where the vulnerabilities will appear. Source
As a trained expert, you should be able to identify vulnerabilities in the software architecture and nip a potential threat in the bud. To do this effectively, you must understand how application data is handled and the potential impact of an attack on the system. Now you know what you need to do, you need tools.
Using existing threat modeling methodology
You don’t need to reinvent the wheel. Even if you are ready to innovate and change the world of cybersecurity forever, there’s nothing wrong with drawing on the expertise of others. Here are three practices you could add to your repertoire.
Attack Trees
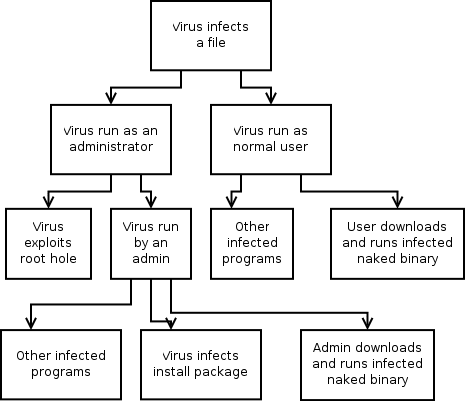
Attack trees are based on your knowledge of malware and adversary behaviour. Source
Unlike the other examples in this guide, an attack tree is a visual representation of the attack patterns that the adversary could use against your application. Much like the attacking half of a playbook, each operationally critical threat should be fully assessed.
In the example above, the threat model describes how a virus could make its way into the system via a range of vulnerabilities. This allows security professionals to understand how potential threats could affect business and security objectives.
DREAD
DREAD was developed by Microsoft employees to assess risk by exploring five categories: damage potential, reproducibility, exploitability, affected users, and discoverability.
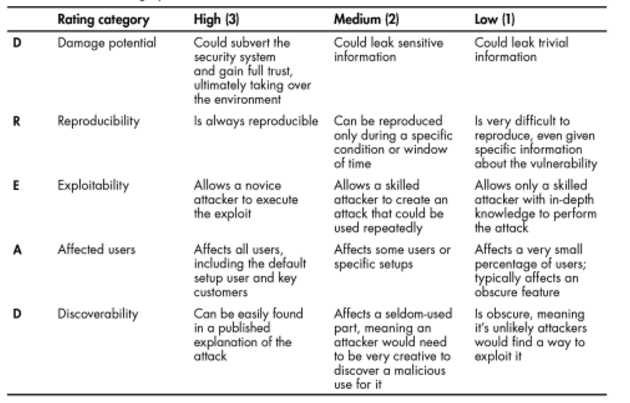
Giving each factor a ranking from one to ten gives you an obvious way to rank threats. Although this risk-centric methodology is no longer used by Microsoft, it is still useful to identify vulnerabilities, potential attackers, and attack vectors.
STRIDE
An alternative threat modelling process used by Microsoft is STRIDE: spoofing identity, tampering with data, repudiation, information disclosure, denial of service, and elevation of privilege.
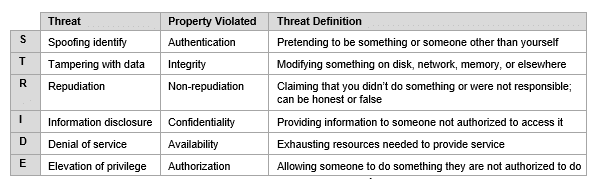
As with DREAD, the STRIDE model is a structured process to create easy to answer questions in your threat model. For example, “how can the attacker access sensitive data?” is a puzzling question but identifying vulnerabilities in the attack tree that would allow the adversary to spoof their identity, tamper with data, and disclose information gives a clear representation of the threat landscape.
Turning practice into workable solutions
Of course, simply knowing what the threats are and how they could attack your systems isn’t enough. You need to start creating solutions to the problems before the product gets released into the wild!
Use your newfound knowledge about the flaws and vulnerabilities to create security measures that stop threats in accordance with the security strategy. Increasing your knowledge of known threats with the Common Vulnerability Scoring System (CVSS) and Common Weakness Enumeration (CWE) as well as best practice solutions with the MITRE ATT&CK Framework will help you deal with any identified threat.
If you want ready solutions to start mitigation, consulting the Microsoft Threat Modeling Tools Mitigation page is an excellent start.
Do you have any top tips for beginners?
If you have some ideas that you think are important for newbies to the world of cybersecurity to understand, send your ideas to the SecPro team.








