Post Credit: Austin Miller
While the world stood still while tensions rise in Eastern Europe, the cybersecurity world has been kicked into overdrive. Not only do we have evidence of nation state attacks against Belarus, Russia, and Ukraine, hacktivists – hackers breaking into systems “for the right reasons” – have gained an uneasy approval from nations all around the world. Virtual war is raging on and cybersecurity professionals need to be on red alert to protect the systems they are responsible for.
Because it is simply impossible to reduce everything down to a newsletter, here are the top stories of the last week. If I’ve missed anything, it’s either because a) the threat landscape is in constant flux, making it impossible to know what is happening or b) the threat landscape has changed since this newsletter was written. If you feel I’ve missed anything important, leave it in our survey at the end of the newsletter and we will do our best to cover it as soon as possible.
Anonymous, anonymous everywhere
Famed for their decentralized model and Guy Fawkes masks, Anonymous has come back from relative obscurity to make itself a name on everyone’s lips as the cyber warfare rages. The technical skill of Anonymous’s hackers has been called into doubt – with numerous Reddit users referring to them as skiddies with LOIC – but the world infamous group seems have been causing real trouble for Russian websites, banks, and government offices.
Among Anonymous’s claims include:
- Shutting down the Russian Space Agency satellites
- Hacking into the computer on Russian President Putin’s yacht and renaming it
- Leaking Kremlin internal documents
- DDoS-ing Russian news sites and running anti-Putin messages and Ukrainian songs in place of planned programming
Although we can doubt the extent that Anonymous as a group have actually achieved these goals, they have certainly been keeping themselves busy since 24th February.
Anonymous faces retaliation
Of course, a nation with the offensive knowledge of Russia would never take Anonymous’s attacks lying down. According to RT (now censored in the EU), a hacking group by the name of Killnet took aim at Anonymous and the websites of Ukrainian governmental officials.
Although sources are slim on this group in English-print media, Russian-language articles about Killnet say that they use a “decentralized botnet” (a world first, in their estimation) to attack and protect clients. As this cybercriminal gang is so new to the scene, it’s difficult to say with much certainty how this attack method actually works. The SecPro will be monitoring their activities going forward.
Although Anonymous isn’t a centralized organization, anonymoushackers.net, president.gov.ua, and a website of a controversial right-wing Ukrainian party was taken offline. Despite promoting their decentralized botnet, it appears that Killnet used DDoS attacks against these targets.
Ukrainian websites facing ten times the number of cyberattacks
In what some people are referring to as the first real cyberwar, a massive wave of attacks was always on the cards. No one has felt the pinch quite as much as the Ukrainians – a tenfold increase in the number of attempted cyberattacks has left many websites based in Ukraine with interrupted service.
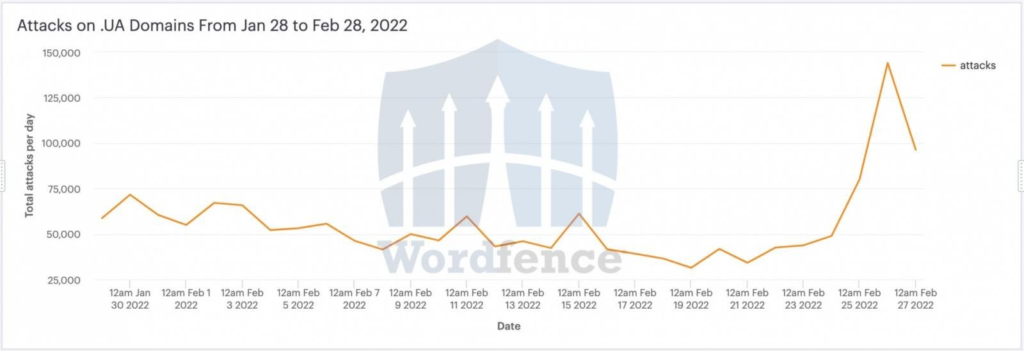
Wordfence, a cybersecurity firm with 8,320 WordPress websites under its protection, recorded 144,000 attacks against Ukrainian domains in a single. And these aren’t en masse DDoS attacks – these are “sophisticated exploit attempts”, according to Bleeping Computer.
Identified as the malware gang “theMxonday”, the adversary has launched a series of hard-to-handle attacks on Ukrainian assets. In response, Wordfence ran a live security feed for .ua websites and prevented attacks against more than 8,000 of them.
Internet Routing Security is undergoing a review by the FCC
Russia’s Cyber Tactics Are Prompting the FCC to Address Internet Routing Security – Nextgov
Network administrators and cybersecurity professionals may have a part to play in an upcoming decision by the US government – is the Border Gateway Protocol (BGP) secure enough to deal with the modern cyberthreats that people all around the globe face every day? Although this reform is being written in the context of the Ukrainian-Russian conflict, it is intended to protect businesses and the average Joe alike from vulnerabilities in email, e-commerce, bank transactions, and VoIP calls.
NIST, the IETF, the Internet Society, and the CSRIC are all backing improvements in global policy in terms of the use of BGP. Establishing secure usage is the central tenet as well as exploring security vulnerabilities in BGP and the possibility of implementing BGPsec on a wider scale.
If you have any views on the topic and wish to make a comment before the review, you can submit a comment here: Russia’s Cyber Tactics Are Prompting the FCC to Address Internet Routing Security – Nextgov
The Conti gang have been compromised
When a ransomware gang gets what’s coming to them, everyone in the cybersecurity world is a bit relieved. When the gang is one as large and notorious as Conti, you know something big has happened. Due to the Conti team’s pro-Russian stance, a Ukrainian security researcher leaked their chat logs to the world.
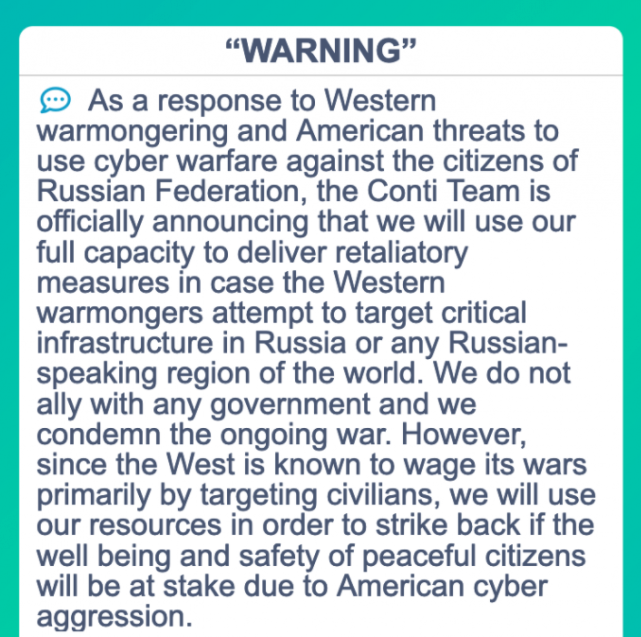
Although the vast majority of the leak is uninteresting to the average person, we can glean a great deal of information about Conti’s TTPs and general business practices from the logs. Contileaks, a Twitter account dedicated to releasing the details of the leak, seems legitimate due to gaps in activity that match with NSA takedowns of the Trickbot botnet and Emotet malware.
For more commentary on the Conti leaks, check out Brian Krebs’s coverage here:” at the bottom of the page








