Exploring Web Vulnerabilities with Damn Vulnerable Web App
Written By: Andy Pantelli
Learning the skills to secure your Web Apps is always a challenge, finding the balance of having a Web App to fully develop & test in a live environment and keeping on the right side of the law can be, well let’s just say open to interpretation. Even spinning up a Honey Pot in an AWS EC2 environment is pushing the boundaries. So how can we get the skills to keep our sites and ecommerce businesses safe?
Fortunately, sites like tryhackeme with labs & tutorials, and Applications like Port Swigger’s Burp Suite Community (Free), Enterprise or Professional Editions and the Academy providing tutorials and techniques provide valuable learning resources.
Today we’re looking at the Damn Vulnerable Web Application which is, quite simply designed to be Vulnerable, and this really is for educational purposes only! Do not upload the site to your hosting provider or any other public facing server! It is after all, damn vulnerable. If you’ve never come across the site before all you need to get started is here https://dvwa.co.uk/

DVWA
Damn Vulnerable Web App is a PHP/MySQL web application designed to be a resource for Security Professionals to test their skills within the law, to help better understand the process of how to secure web applications within the legal boundaries. DVWA is freeware and can be distributed under the terms of the GNU General Public Licence as published by the Free Software Foundation. As previously stated, do not install in any live environment. DVWA is damn vulnerable! The Application aim is for you to practise some of the most common web vulnerabilities in a controlled environment. Whilst most of the Application vulnerabilities found in DVWA are documented, it is encouraged that you try and discover as many or additional undocumented vulnerabilities that may exist.
DVWA has number of attacks that you can simulate to help you learn the techniques that attackers may use against your Web Apps or Server, including;
- Command Injection
- File Inclusion
- Brute-force
- SQL Injection / SQL Injection (Blind)
- CSRF
- Weak Session IDs
- File Upload
- Insecure CAPTCHA
- XSS (DOM)
- CSP Bypass
- XSS (Stored)
- XSS (Reflected)
This article will show you how to deploy DVWA within a Docker Container. Firstly you’ll need to have Docker installed. If you don’t have this set up a complete guide to Docker can be found at https://docs.docker.com/get-started/overview/ – Docker is used to create, deploy run applications within a Container which allows the developer package applications libraries, dependencies then deploy it as a complete package. I won’t focus too much on Docker in this article but if you want or need to learn more visit the getting started page that I linked to earlier but briefly to install Docker
sudo apt update
sudo apt install –y docker.io
sudo usermod -aG docker $USER
# reload to ensure permissions update then issue the command below
newgrp docker
Whilst there are a number of DVWA versions available but the only supported version is the latest source code from the GitHub repository:
git clone https://github.com/digininja/DVWA.git
Now that you have Docker installed, and DVWA downloaded let’s run our image
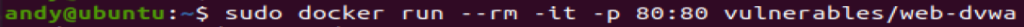
We should now have DVWA running and quickly checking from your browser you should be presented with the App Login page
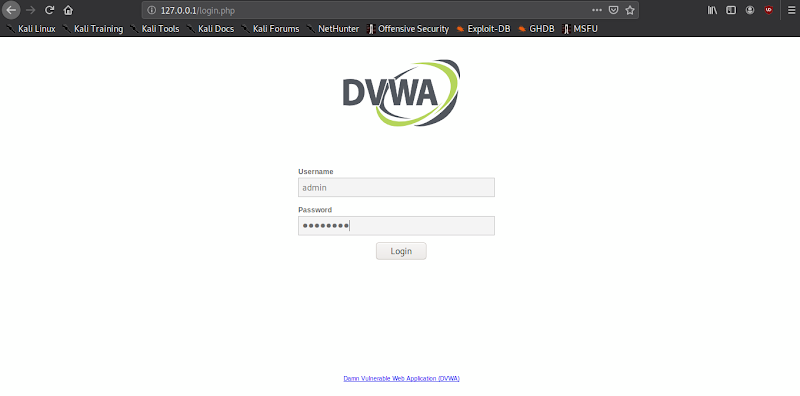
The next step is to follow the prompts to set up DVWA and create the DB.
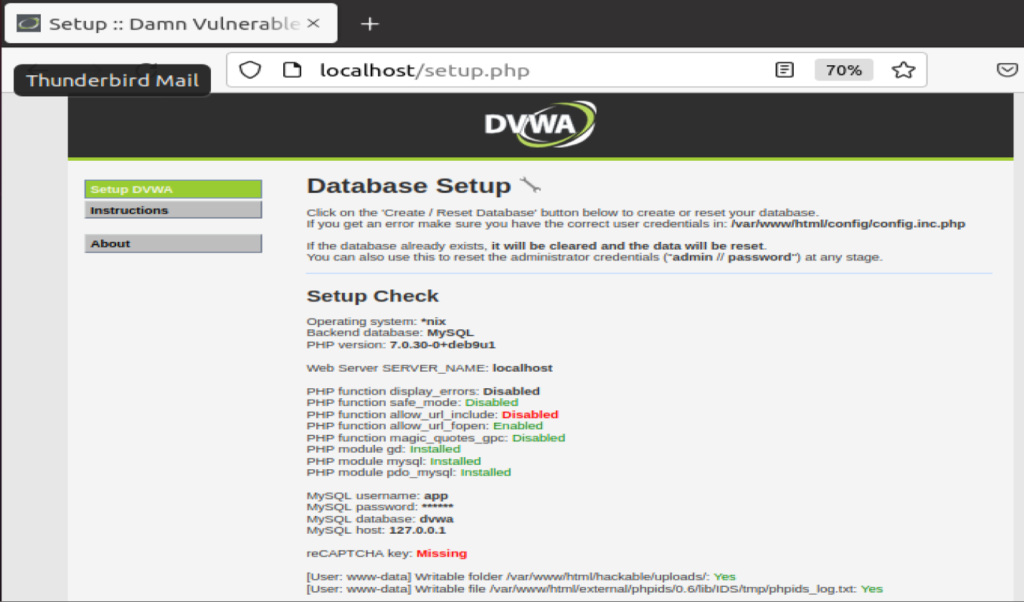
You will then be logged out before having the App, DB and attack tools available to you.
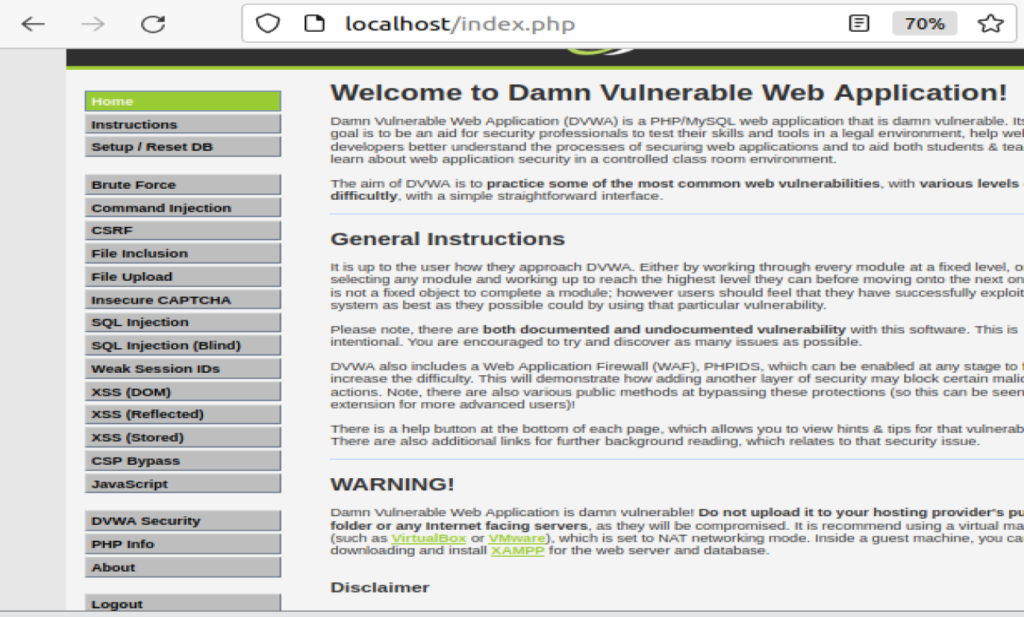
DVWA has several configurable Security Levels to test your skills, by selecting the more difficult options you can control the vulnerability levels of DVWA to test your skills
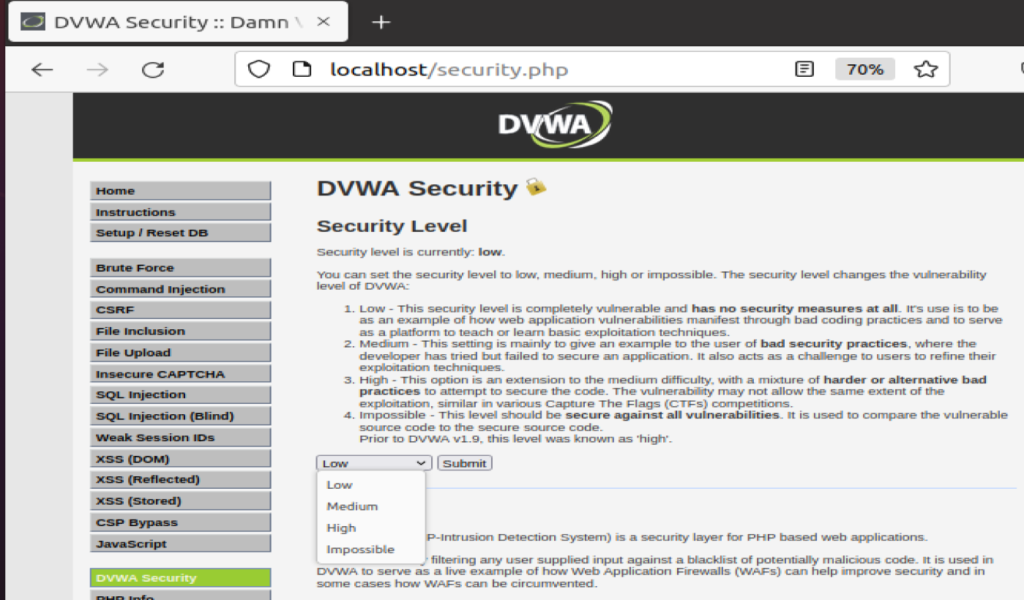
There you have it, a vulnerable Web Application built on PHP/SQL that you can explore, investigate, discover and learn from. DVWA can be found on GitHub with the resources that you would expect. The Application home page can be found here https://dvwa.co.uk/ with direct links to download and also to the GitHub Source Code.
DISCLAIMER
Damn Vulnerable Web Application – like already stated is damn vulnerable. Do not under any circumstance upload the App to a public facing directory or other internet facing server as they will be compromised! Running the application in Docker or other virtualised environment is highly advised.
The Application is designed for educational purposes, simply put to learn or understand attack methods and attackers. DVWA can help Security Professionals of all levels to learn ethical hacking or Penetration Testing skills. In providing this tool great credit goes out to Ryan Dewhurst who created this application way back in 2009 whilst still at University and releasing it as an Open Source project. Ryan has since handed over the reins to his old friend Robin Wood who now manages the Project. Although created way back in time, DVWA is still as relevant today as it was then as shown by vulnerabilities such as SQL Injection still being one of the most common attacks.








