In penetration testing, wordlists play a great role. Every good penetration tester will have their own set of wordlists which they use for different purposes. The success of a dictionary-based attack lies in how good the given wordlist is. There can be different wordlists for different purposes. You cannot use a password wordlist in a directory brute-force attack. Similarly, a wordlist meant for SSH brute force cannot be used for web-application login brute force. Hence, it is important to have different wordlists for different purposes.
SecLists is one of the most preferred wordlists by many penetration testers. SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
Download SecLists from here: https://github.com/danielmiessler/SecLists
But what if you need to create your own custom wordlist? In this article, we will see 4 tools that you can use to create your own custom wordlist. Previously I shared an article on how to use Cewl to create a wordlist based on a website.
- Crunch:
Crunch is a great tool to generate a wordlist according to your requirement. With this tool, you can give a maximum and minimum length to the password and provide it with a character set for use while creating the wordlist. The minimum and maximum length feature come in handy when you know the password policy of the application you are about to test.
Download it from here: https://github.com/jim3ma/crunch
To install the crunch tool use the following commands as per your Linux distribution.
In case of Debian/Ubuntu
$sudo apt-get install crunch
In case of CentOS/RedHat
$sudo yum install crunch
In case of Fedora OS
$sudo dnf install crunch
The good news is that crunch comes pre-installed in Kali Linux.
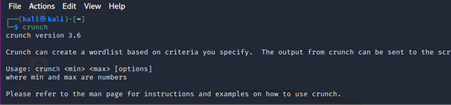
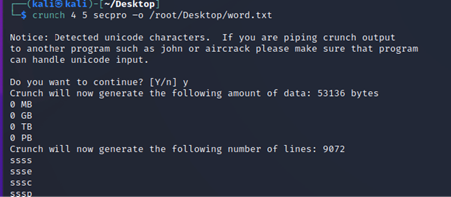
Here is the syntax to run the tool:
crunch <min> <max> <character-set> -t <pattern> -o <path>
- Cewl
It’s human nature to use the words that we use in our everyday life, as those words will first pop into their heads when considering passwords. And we can use this fault in human nature to create a custom wordlist which we can then try out in brute-forcing passwords.
For making such a custom wordlist we will use a tool called Cewl. Cewl is a Ruby program that crawls a URL to a defined depth and produces a list of keywords that can be used as a wordlist. And it is highly effective.
Download Cewl from here: https://github.com/digininja/CeWL
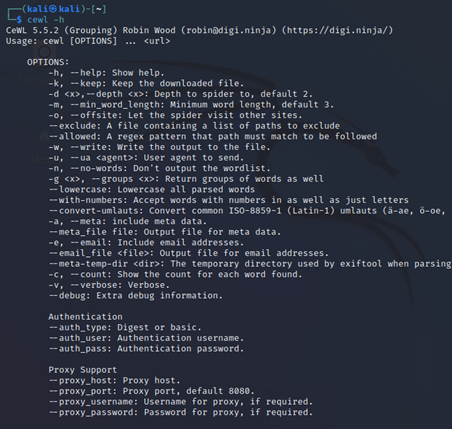
Syntax: cewl <url> -d<depth> -w<path>
<url> – Give the URL from where you want to grab the words
–d <depth> –Define the number of links you want it to go through while creating your dictionary.
-w <path> – path to store all the possible passwords.
- Cupp
This is a third-party tool developed in python which can be used for creating a wordlist for password cracking. This is a different tool from the above two. In other to use this tool you need to have some knowledge about your target and must know few details about the target like date of birth, child’s name, etc.
People often follow a similar pattern while setting a password. They add their date of birth, age, child’s name, etc while creating the password and this tool focuses on this very weakness and helps in cracking passwords effectively.
Before creating the wordlist, it will ask you a few questions about the target.
Download from here: git clone https://github.com/Mebus/cupp.git
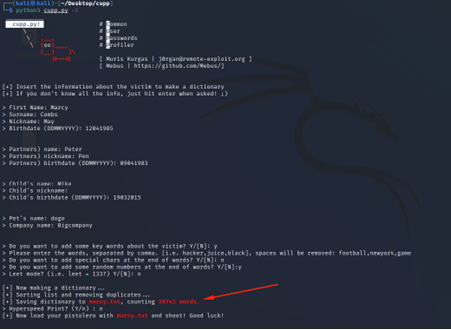
I then added some random details:
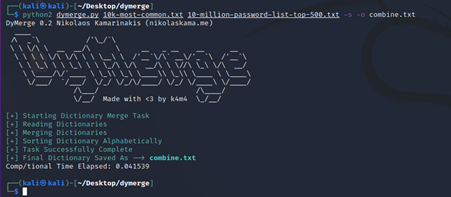
- Dymerge
This is the last tool on our list today. This is not exactly a wordlist generator but as the name suggests it can merge multiple wordlists into one. It is a simple, yet powerful tool – written purely in python – which takes given wordlists and merges them into one dynamic dictionary that can then be used as ammunition for a successful dictionary-based (or brute-force) attack.
As you might have seen in Seclists there are multiple wordlists. You can combine multiple wordlists together and create one single file and can test for password attacks.
Installation:
- git clone https://github.com/k4m4/dymerge.git
- cd dymerge/
- python dymerge.py
Syntax:
python dymerge.py <path> <path> -s –o <path>
Here in this example, I combined SecList’s 10k most common passwords and 10 million password list top 500. You can combine more than two files as well.