SecPro #18: The BrakTooth Vulnerability, Azurescape, Brute-forcing FDE
Hey there. In this issue:
- Trending Security Issues
- The BrakTooth Vulnerability: Bluetooth Comes to a Crashing Stop
- Brute-Forcing Full Drive Encryption
- Critical Vulnerabilities in Windows
- Secret Knowledge: Building Your Security Arsenal
- The SecPro Quiz
Trending Security Issues
Azurescape: Cross-account container takeover
It was recently uncovered that a chain of exploits could allow malicious Azure users to infiltrate other customers’ cloud instances within Microsoft’s container-as-a-service offering. “Azurescape” allows malicious users to compromise the multitenant Kubernetes clusters hosting ACI, establishing full control over other users’ containers.
This research from Palo Alto Networks presents an analysis of the issue, and suggests best practices for securing Kubernetes, with a focus on multitenancy, that could help prevent similar attacks.
How attackers are hiding in proxyware
Adversaries are finding new ways to monetize their attacks by abusing internet-sharing or “proxyware” platforms like Honeygain and Nanowire. This poses new challenges to organizations, especially to those whose internet access is rated as residential. But any organization could be at risk, as there are platforms that also allow data center-based internet sharing. Malicious actors are taking multiple avenues to monetize these new platforms in their favor. This post from Talos Intelligence discusses the adversarial abuse of proxyware in depth.
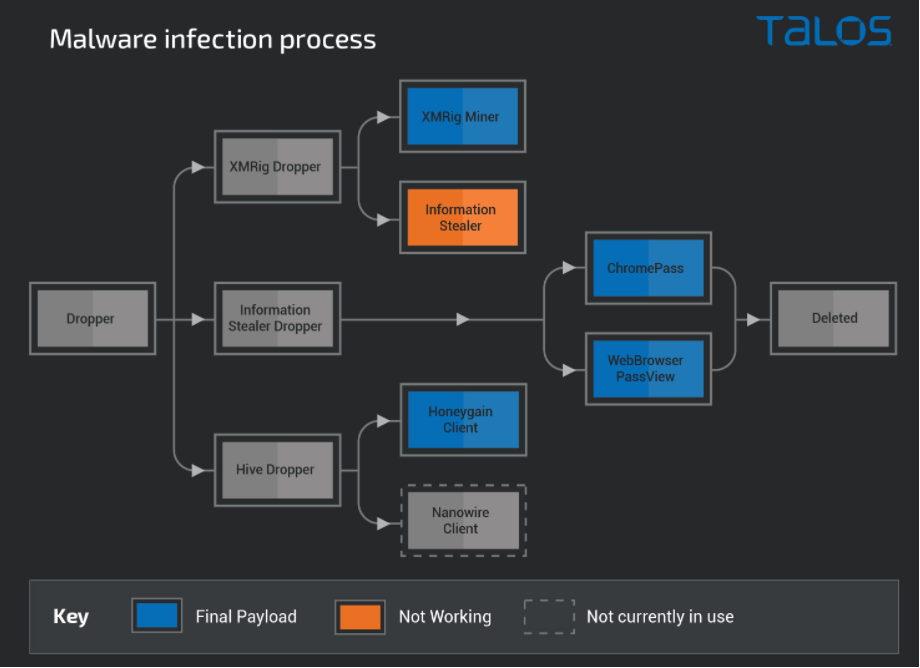
Execution flow of how malware campaigns monetize successful infections
With the cloud computing market expected to grow to over $940 billion by 2026, building suitable cloud infrastructure and allocating the correct number of cloud resources is a top priority. But it is a difficult task for any security team.
DevOps practices are practically everywhere these days, but why are the same old security issues not being handled earlier in the SDLC (especially in the cloud!) when security teams are adopting better processes and better tools?
The truth is that development and operations teams still haven’t fully learned how to secure software and secure code. Creating secure apps takes much longer than agile needs allow when security teams have to pick up the slack when the cloud applications are already made. That’s why we need a revolution in the development world – a DevSecOps revolution.
IoT Security
The BrakTooth Vulnerability: Bluetooth Comes to a Crashing Stop
By Austin Miller
If you’re lucky enough to own a device with an ESP32 SoC installed on it, this one’s for you. A team of security researchers from the Singapore University of Technology have found a series of vulnerabilities that allow man-in-the-middle attacks on all Bluetooth devices. They’ve decided to call it BrakTooth
Although there are a number of mobile phones and laptops (most notably including Windows Surface personal computers) at risk because of the 16 BrakTooth vulnerabilities, a larger number of industrial and IoT devices are also at risk. Potentially billions of devices have these security vulnerabilities unpatched, leaving them exposed to denial of service attacks.
Let’s find out how it works.
BrakTooth Vulnerability: Breaks ‘Tooth
Brak is the Norweigan for “crash” and that is basically what these flaws cause – crashes and denial of service in devices that are using the vulnerable chip.
BrakTooth is not a single vulnerability so much as a family of security vulnerabilities that are found in 13 chips from 11 vendors. The most serious of these vulnerabilities (CVE-2021-28139) came from the Espressif ESP32 chip, commonly found in industrial and IoT devices.
List of chips affected with BrakTooth vulnerabilities
BrakTooth Vulnerability: Source
It would be unfair to leave all the blame at Espressif’s door, however. The Qualcomm WCN3900 from Arrow and the Intel AX200 SoCs also come from high-profile vendors, which leads us to ask: why was this flaw allowed to go to production by highly regarded distributors?
How does CVE-2021-28139 work?
When a device connects over Bluetooth, compliant LMP firmware stops out-of-bounds write errors through checks. If an out-of-bounds write attack comes to a well-configured system, it will be stopped at (for example) the buffer.
Because there is no out-of-bounds defense in place on the ESP-IDF 4.4 chip, attackers can inject arbitrary code via a man-in-the-middle attack. These arbitrary code execution attacks may simply cause a device to crash or it could be a jumping-off point for an attacker.
An illustration of CVE-2021-28138
The CVE-2021-28139 exploit in action (Source)
As these chips are often found in IoT (which are often weak points in a network anyway) and industrial devices, injecting code through this Bluetooth vulnerability could lead to attackers gaining control of an entire system.
You can see a BrakTooth attack in action here: https://youtu.be/F7VjuOiUsNk
As you can see from the demonstration, the ACE attack undermines the intended functionality. The LED is no longer controlled by the phone – now imagine that on an industrial scale with an industrial tool!
A similar demonstration found here shows that the BrakTooth vulnerability can be leveraged to crash firmware and cause connected Bluetooth devices to crash. Again, apply that to a production scale and an organization would be in serious trouble.
Has BrakTooth Caused Much Damage?
Thankfully, this Bluetooth vulnerability was found by security researchers at the Singapore University of Technology. Instead of exploiting potentially billions of devices, they chose to write about how these flaws are a security risk and how the vulnerabilities affect normal Bluetooth operations (at least in theory).
The team waited for the vendors who had sold these faulty chips to release patches before publishing the Proof of Concept (which can be found here). Because of this decision, Bluetooth devices around the world are safe from Denial-of-Service and Arbitrary Code Execution attacks (at least one’s coming from this set of vulnerabilities…)
How Do I Protect Myself Against BrakTooth?
For people with devices that contain any of the affected chips, there is a two-part plan for defending against attackers: a) find the relevant patches for the firmware installed on your device and b) adopt best practices.
If you have a personal device such as Xioami smartphones or a Windows Surface personal computer that is using one of the affected chips, the best practices are to:
- Update all systems which house the chip, using a patch provider by the appropriate vendor
- Ensure that Bluetooth is turned off when not in use
- Only use Bluetooth when you are in a safe area, preferably at least 300 feet away from crowded areas where potential threat actors could be hiding
By installing the appropriate patch and following Bluetooth best practices, any device that is affected by BrakTooth can be safely and securely used. The patch is important, no one is going to deny that.
But as we know from the KNOB and SweynTooth vulnerabilities, new exploits over Bluetooth are always just around the corner. Maintain Bluetooth best practices in your day-to-day life and you will stop malicious actors attempting to leverage vulnerabilities in your devices.
Want to find out more about BrakTooth Vulnerability?
The ASSET Research Group’s write-up on the vulnerability can be found here as well as links to their PoC and detailed technical illustrations.
Additional reading on BrakTooth and similar Bluetooth attacks:
- MalwareBytes – BrakTooth Bluetooth vulnerabilities, crash all the devices!
- ASSET Research Group – SweynTooth: Unleashing Mayhem over Bluetooth Low Energy
- José Lopes Esteves – BlueMirror: Reflections on Bluetooth Pairing and Provisioning Protocols
- KNOB Attack
Cryptography/Tutorial
Brute-Forcing Full Drive Encryption
By Karl Gilbert
Full Disk Encryption (FDE) is the encryption of all data on a hard drive device using an encryption key. Once a drive is encrypted, all data is automatically encrypted before writing it to the disk and all read operations automatically decrypt data before returning it to the system. Full disk encryption encrypts the entire hard drive including partitions like swap files, system files, and hibernation files. If an encrypted hard drive is compromised, the encryption of the drive remains unchanged, and only an authorized user can access it.
There are several attacks on FDE systems, which are commonly used in forensic activities. In this tutorial, we’re going to look into the brute-forcing methodology of attacking fully encrypted drives for….
Read the full tutorial HERE.
Vulnerabilities & Exposure
Critical Vulnerabilities in Windows
Last month, four critical flaw update packages were rolled out by Microsoft along with a few more serious ones. Here’s a breakdown of the most severe vulnerabilities that Microsoft caught in time.
Microsoft Windows Security Update for August 2021
The security update for August contains some interesting vulnerabilities that Microsoft has quickly rolled patches out for. Notable inclusions within the package are:
- CVE-2021-26424 – a TCP/IP remote code execution vulnerability which Microsoft stated would allow an adversary to remote gain control of and edit files over the TCP network.
- CVE-2021-26426 – a vulnerability that would allow an attacker to gain escalated permissions to a system either locally or over SSH through a weakness in a user’s Windows profile picture.
- CVE-2021-26432 – another remote code execution vulnerability, this time affecting users who had downloaded the NFT on a server. Through the vulnerable rpcxdr.sys, an attacker could gain access to an entire system.
- CVE-2021-36948 – a zero-day that allows both escalations of privileges and remote code execution through the Windows Update Medic Service. Windows acknowledges that this vulnerability has been exploited.
Also included were Printer Spool vulnerabilities and 7 Critical Flaw fixes. It has been a busy month for Microsoft.
CVE-2021-34478
The Microsoft Office Remote Code Execution Vulnerability is a vulnerability in Microsoft Word that allows an attacker to remotely execute code.
By downloading and running a .doc(x) file with the vulnerability in the glTF-SDK component, the attacker causes a buffer overflow. There is no validation of user-supplied data, allowing remote execution of code in a similar way to a Macro virus attack.
Microsoft stated that this vulnerability has not been exploited by attackers and that exploitation is now “less likely”.
CVE-2021-36942
Also known as the catchy Microsoft Windows Local Security Authority (LSA) Spoofing Vulnerability August 2021, this critical update was necessary because a malicious actor could trick a domain controller to authenticate with another server. The unauthenticated user would be able to seize control of a remote server and its domain controller by using NTLM.
Microsoft advised that urgent updates are rolled out to servers and especially domain controllers. Additional advice for protecting servers and domain controllers was also released in KB5005413, especially in relation to protecting against PetitPotam (Github repository here).
Microsoft .NET Core and ASP .NET Core Security Update for August 2021
Consisting of a Denial of Service vulnerability, this core security update was rolled out as a Critical Flaw. CVE links to the three vulnerabilities can be found here:
Similar to the other vulnerabilities in this rollout, there is a risk of information leaking through CVE-2021-26423. But there is also a serious risk of denial of service through .NET core and ASP .NET, meaning this update is recognized as important by Microsoft for both server and home systems.
Want to know what else has changed?
Along with the four critical packages listed above, there were a number of less severe patches released in August as well. Find the rest of Microsoft’s August updates here.
Secret Knowledge: Building Your Security Arsenal
Discover useful security resources, threat intel, cheatsheets, and open-source CLI/web tools.
Vulnerability & Attack Modelling
STIX 2.0: Structured Threat Information Expression (STIX), is both a serialization format and a language that may be used to trade CTI or cyber threat intelligence, aiding security professionals and IT personnel in understanding different attacks and vulnerabilities. Features include:
- Share CTI with other organizations
- Learn about attack patterns, identity, intrusion set, malware, and threat actors
- Collaborative vulnerability and attack analysis
CAPEC: Common Attack Pattern Enumeration and Classification (CAPEC), allows you to understand the attack patterns used by cybercriminals and hackers. Features include:
- Analyze attack patterns
- Descriptions of attacks and possible solutions
- Discover related attack patterns
Hunting & Investigations
GRR Rapid Response: GRR Rapid Response is a tool used for investigations and forensics, allowing you to respond to incidents by getting live forensics remotely. SecOps professionals can assign different levels of urgency to attacks and analyze the situation remotely. Features include:
- Gathers and processes data from many machines and devices
- Use GRR to remotely check on machines
- Analyze one or more machines for vulnerabilities
OSSEC: OSSEC can watch and analyze everything from FTP servers, to mail servers, databases, web applications and servers, firewalls, antivirus, event logs, remote access logs, helping you know whether your system is breached. Features include:
- Analyze logs, check system integrity, monitor Windows registry, detect rootkits, and more
- Issues threat alerts
- Compatible with Windows, OS X, and Linux
Other Resources
How to find more vulnerabilities in APIs through fuzzing: API Hacker Alissa Knight and Detectify share new research on the efficacy of fuzzing as part of the web penetration testing toolkit and especially of APIs. The full research report provides technical evidence and a detailed walkthrough of how the fuzzing of APIs was conducted. Some of the tools used include OpenAPI, Kiterunner, and RESTler. The results are available in this downloadable whitepaper.
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes.








